Sync with Microsoft Azure AD/Entra ID
This describes how to set up Foxpass to sync your directory with Microsoft Azure AD/Entra ID.
Authorize your Foxpass account with Azure AD/Entra ID
Go to the Foxpass 'Sync' page. Go to the Foxpass 'Sync' page. Click on the dropdown next to 'Select synchronization provider' and choose 'Microsoft Entra ID'.
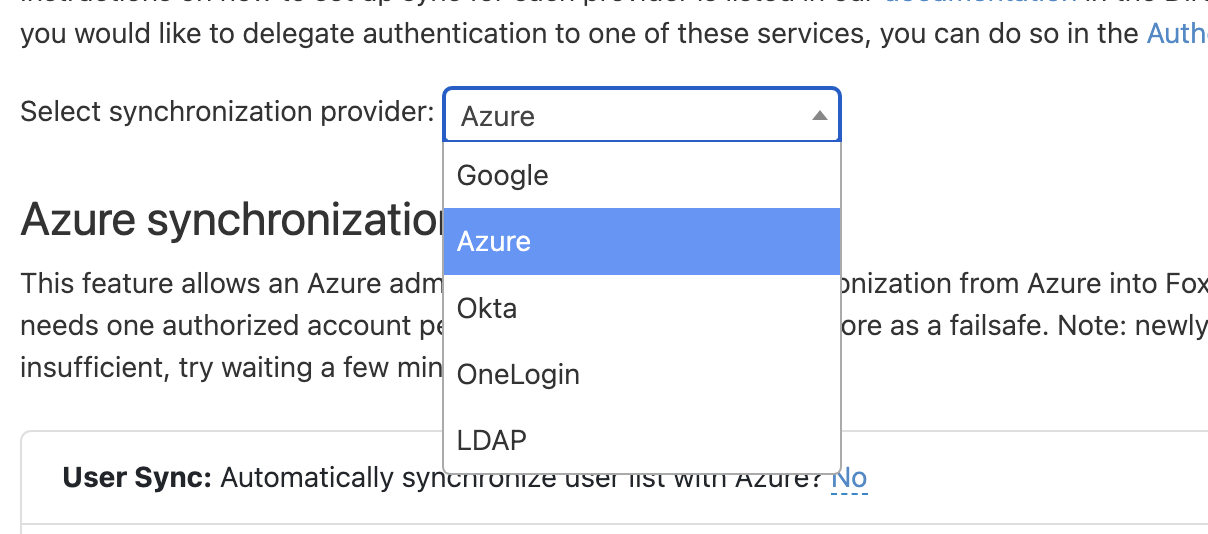
Choose Azure
Sync Users
For User Sync, choose 'Yes' from the dropdown menu, click 'Authorize Account for User Sync' button. Azure will then ask for offline access to your data, which Foxpass needs to access the directory data.
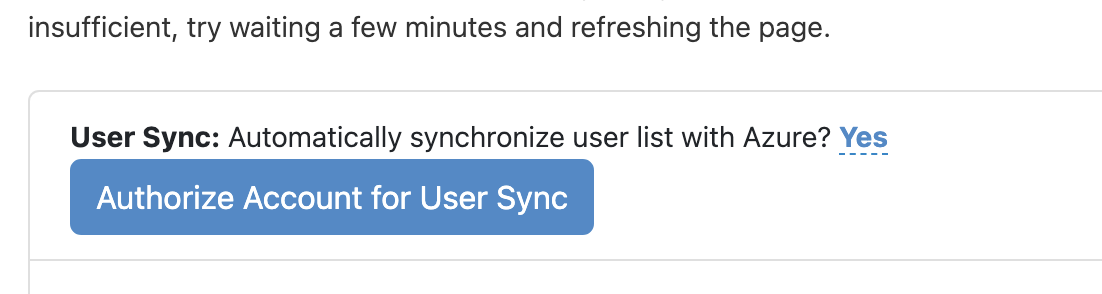
Authorize user sync
Click "Accept" and you will be redirected to Foxpass.
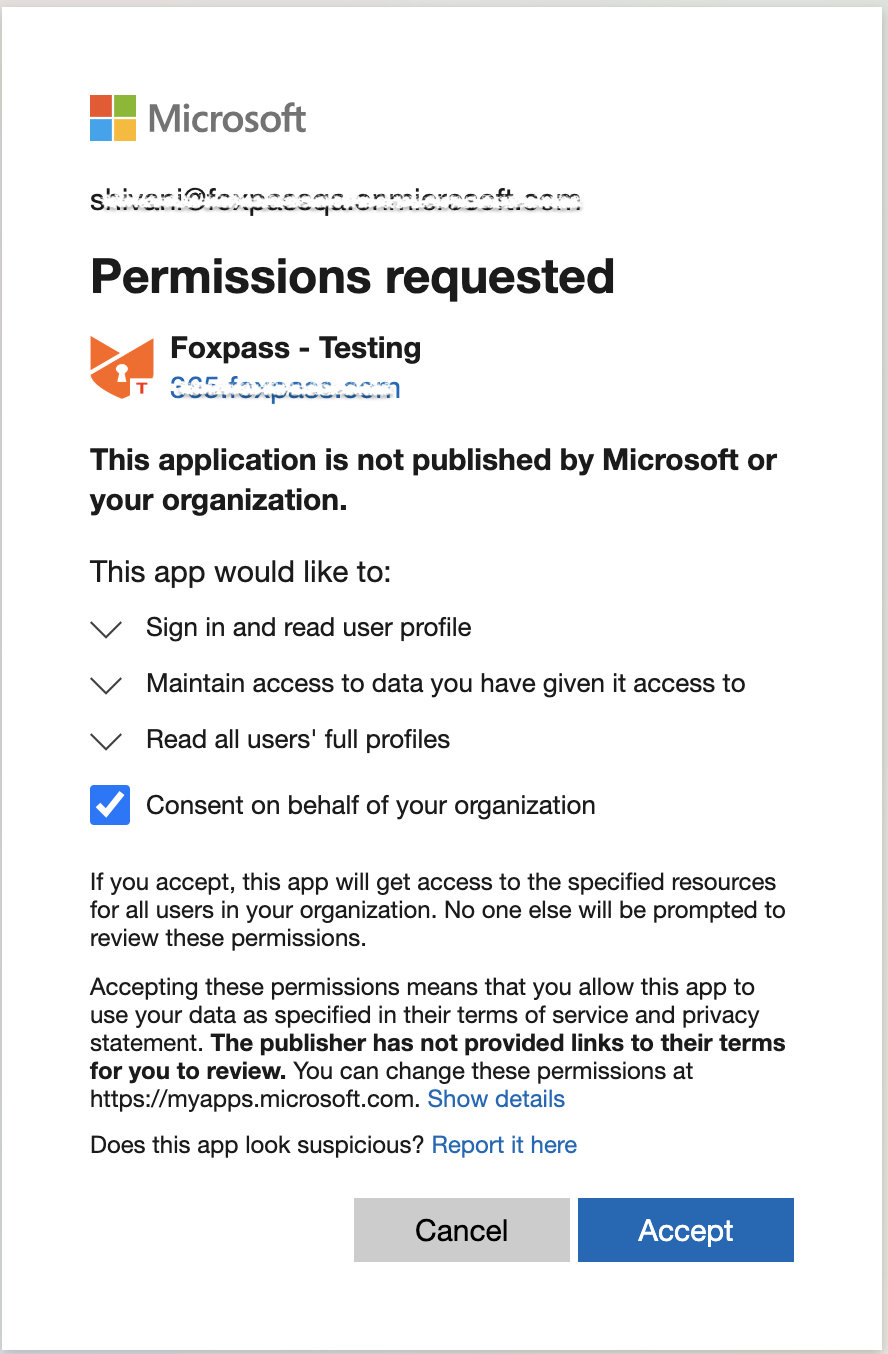
Click Accept
If you see a green checkmark at the top of the page, your credentials are good to go.
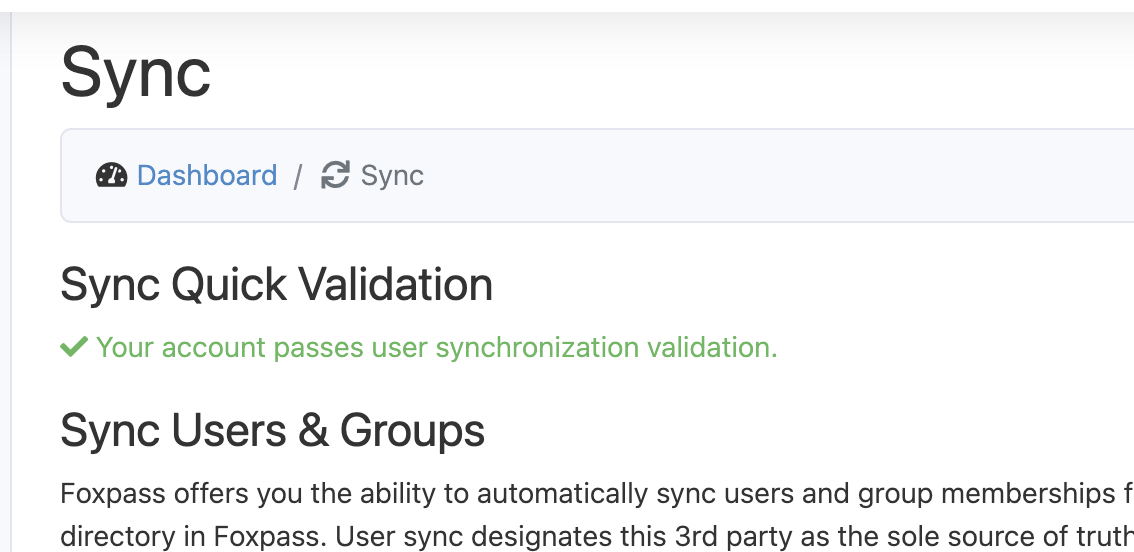
Account passes sync validation
Click on 'Sync now' button. You will see a message saying ' Sync initiated successfully'. Click Ok and you can see the status of your sync in the table as shown in the picture below:
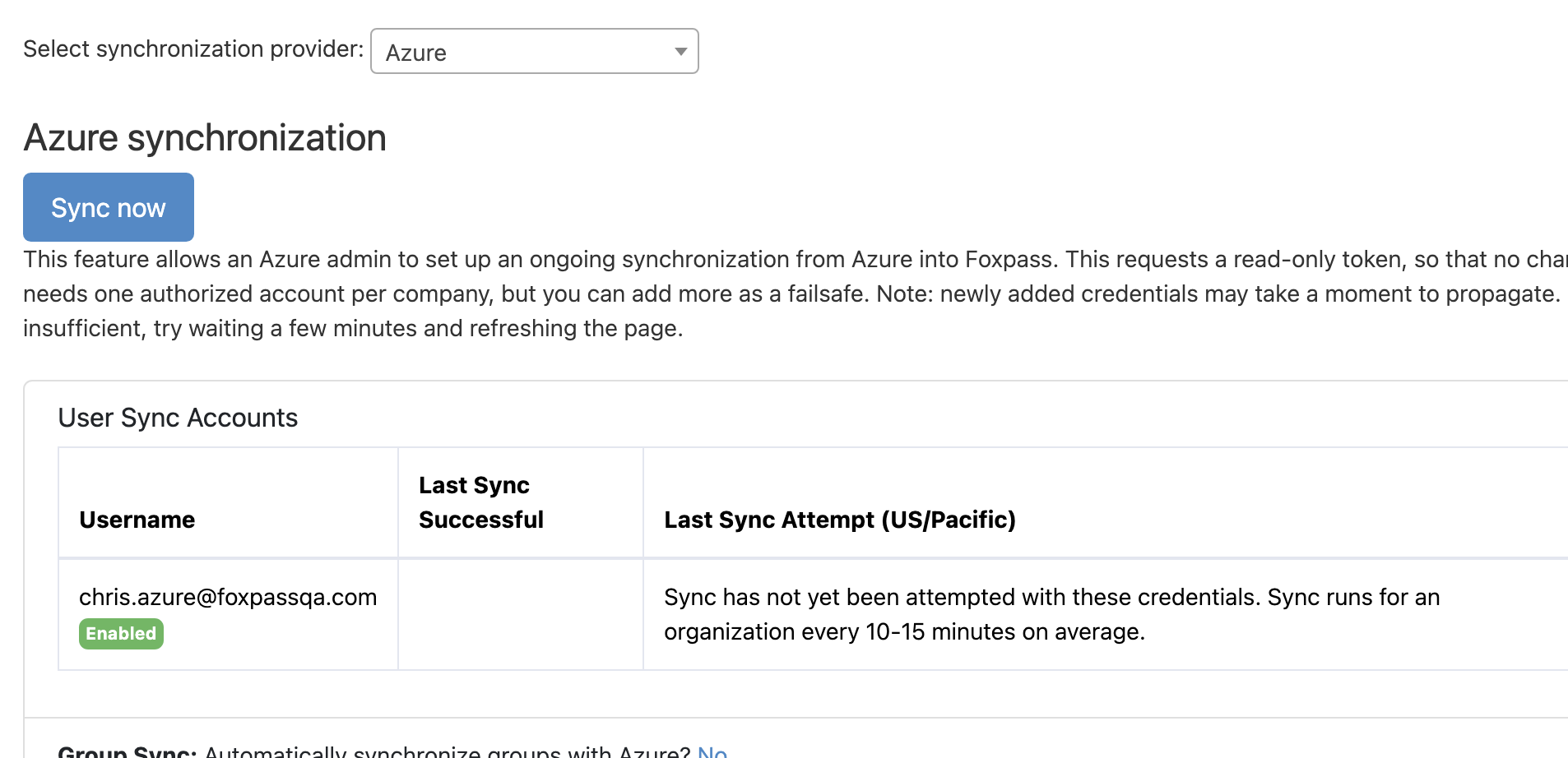
Sync status
Now, you can see synced users on the Users page.
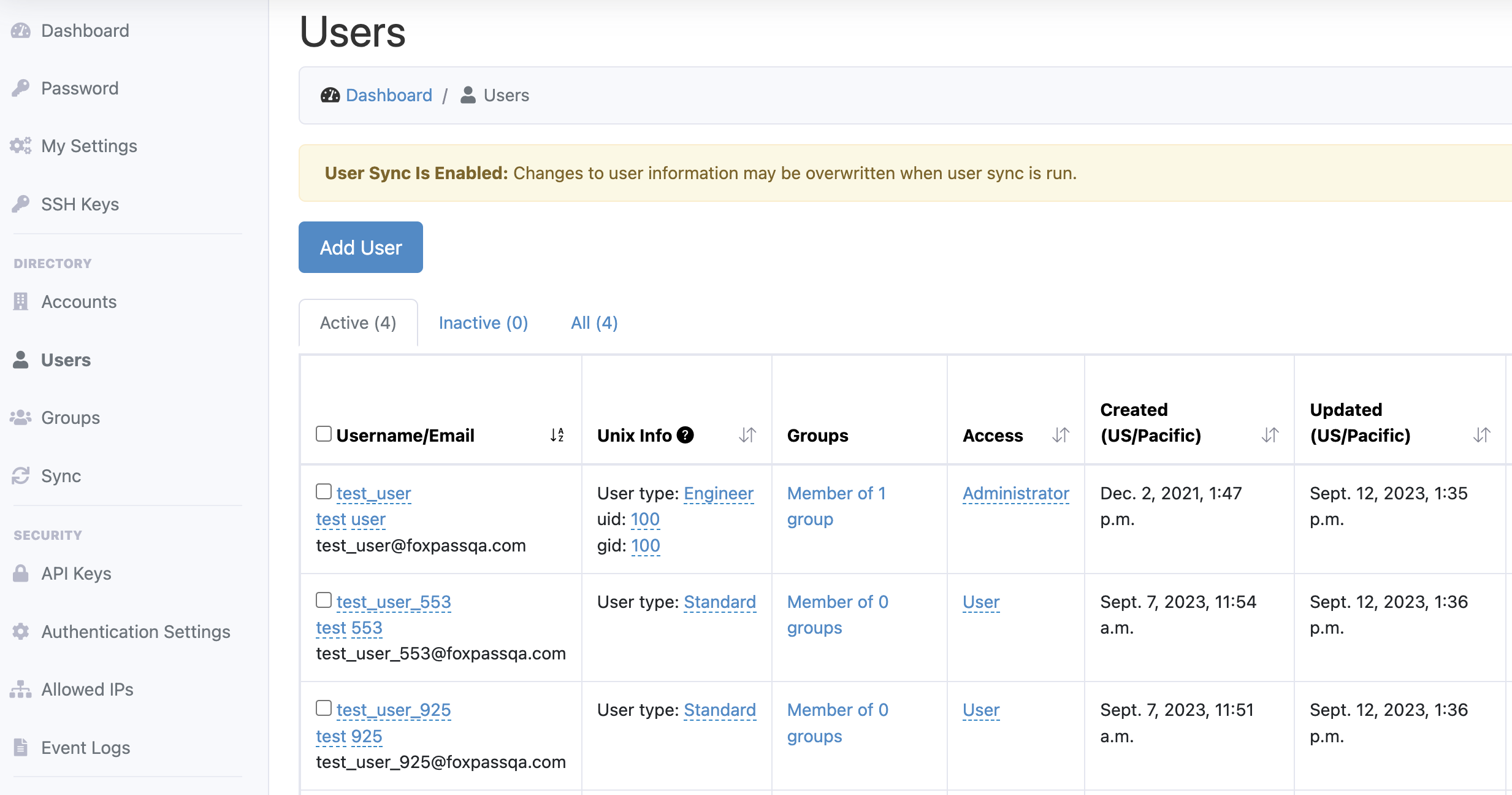
Sample Users page with synced users from Azure/Entra ID
A Note about Admin Permissions
Foxpass needs a specific set of Azure/Entra ID Administrator permissions in order to sync. A Global admin role works best, but you'd like to assign a minimal set of roles you can assign the Cloud application admin and User admin roles in tandem.
We recommend adding a second set of credentials as a back up in case the first set fails. This can happen when the administrator who authorized the sync leaves the company and has their Azure AD/Entra ID account disabled. You can authorize another set of credentials by having another administrator log into Foxpass and click the "Authorize Account for Sync" button.
If you have Azure Conditional Access policies enabled, make sure that they allow requests from Foxpass's servers.
Sync Groups
Select 'Yes' from the dropdown for 'Group Sync' option, authorize account for group sync and then click 'Sync Now' button. The Azure/Entra ID groups will be synced to Foxpass and can be seen on the Groups page.
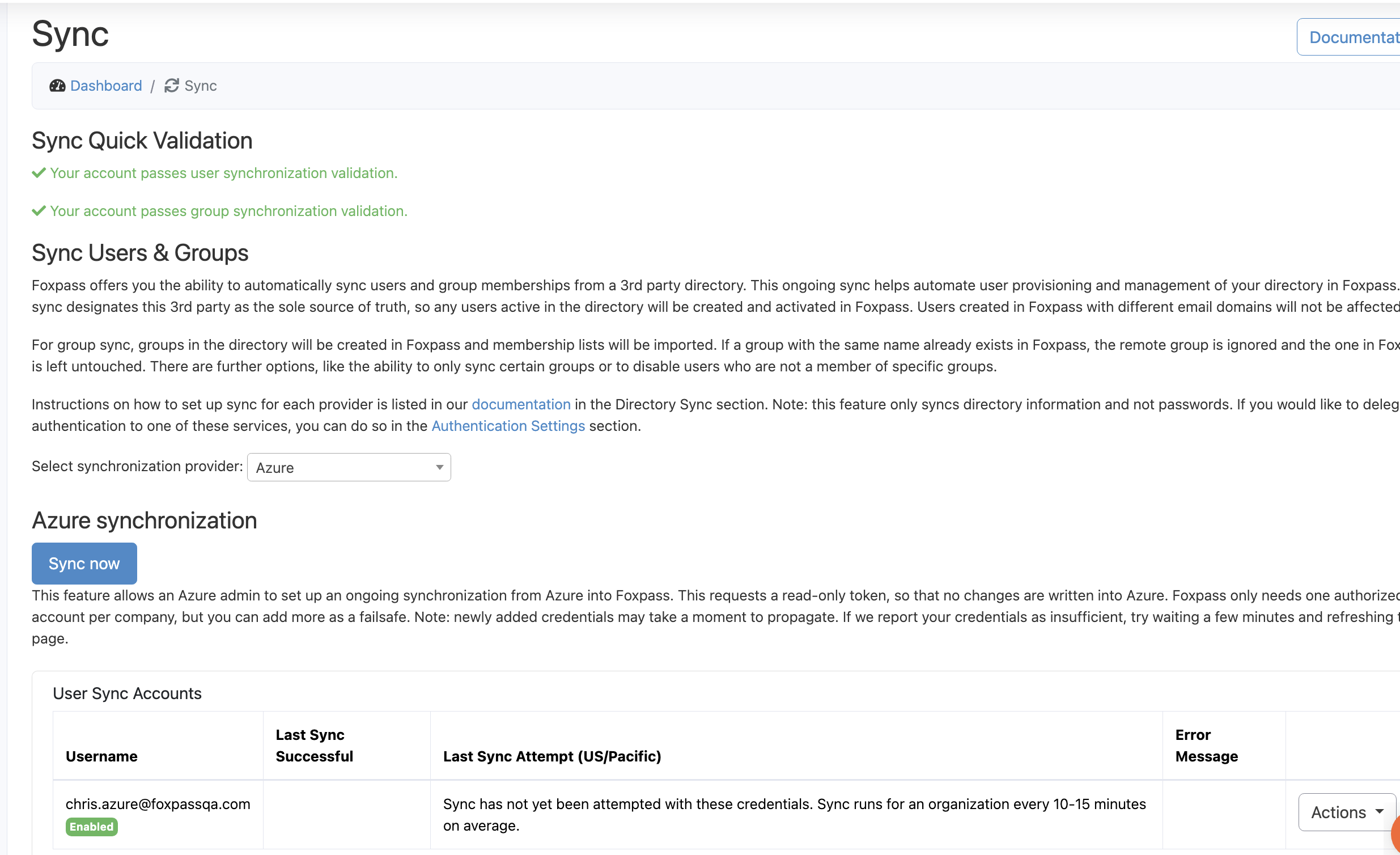
Note: Make sure your groups are ready for sync
Groups created in Azure AD/Entra ID won't sync from Microsoft's Graph API. Additionally, groups without an email (like Security groups) do not sync with Foxpass by default. Read this documentation to learn more about the different types of Azure AD/Entra ID groups.
If you're not sure if your groups will work for sync, use the "all groups in my organization" endpoint in the Groups section of the Microsoft graph API explorer to see if the group is both returned from the API endpoint and has a mailing address associated with it.
If you would like to sync Security groups or other Azure AD/Entra ID groups that do not have an email associated with them, enable the Sync Groups Without Emails feature on the Sync page after configuring Group Sync.
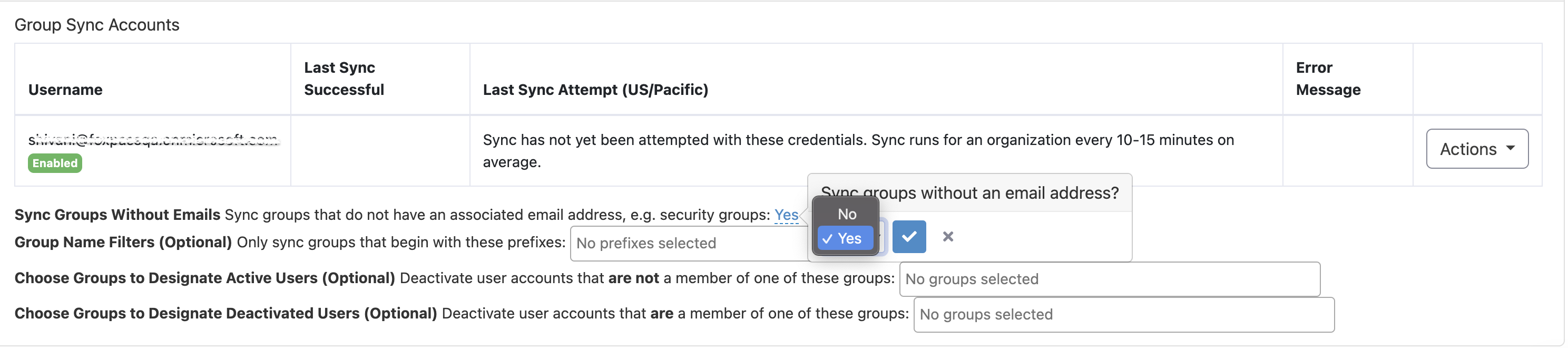
Select 'Yes' to Sync groups without emails
Optional: Enable Group Sync Allowed list
If you have group sync enabled, you can have allowed list of groups, which get imported during sync. This is useful for organizations that only want to import a subset of their groups used in Foxpass. Once group sync is enabled, you'll see a field to add any group prefixes for adding to allowed list. During the group sync process, any groups that do not begin with that prefix are not synced with Foxpass.

Sample Group prefixes
Optional: Enable Allowed User list via Group Membership
If you have group sync enabled, you can add allowed users that belong to specific groups. This is useful for organizations that only want a subset of their directory to have access to Foxpass. Once group sync is enabled, you'll see a field to mark any groups which are allowed. During the group sync process, any users that are not a member of one of those groups are automatically marked as "inactive."

Sample allowed user list via group membership
Optional: Enable Non Allowed User list via Group Membership
If you have group sync enabled, you can have a list of non allowed users that belong to specific groups. This is useful for organizations that have a large number of machine or role accounts that don't need access to Foxpass. Once group sync is enabled, you'll see a field to mark any groups to be ignored from syncing. During the group sync process, any users that are a member of one of those groups are automatically marked as "inactive."

Deactivate users in the specified groups
Optional: Configure subdomains
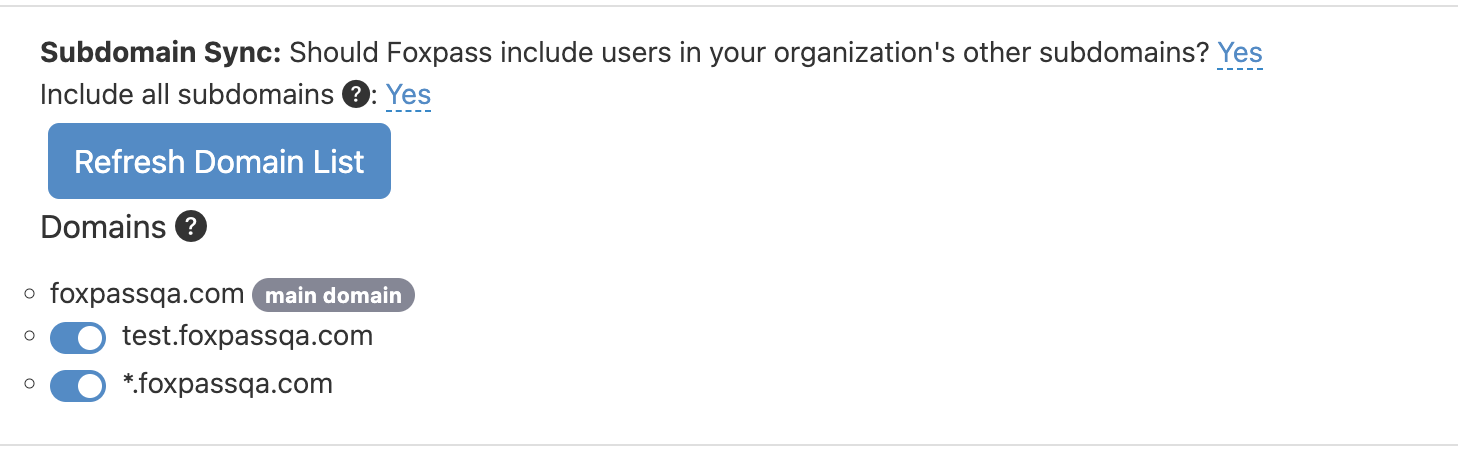
Foxpass allows you to configure subdomains from Azure AD/Entra ID. Click on 'Yes' option for 'Subdomain Sync' and authorize the account for domain sync.

Authorize account for Domain sync
Choose 'Yes' for 'Include all subdomains' option if you want to include all domains in the wildcard format *.foxpassqa.com. For example: contractors.foxpassqa.com or corporate.foxpassqa.com. Click on 'Refresh Domain List' if needed.
Include all subdomains
Updated 5 months ago
