Foxpass Linux debugging
How to track down issues with Foxpass's Linux integration
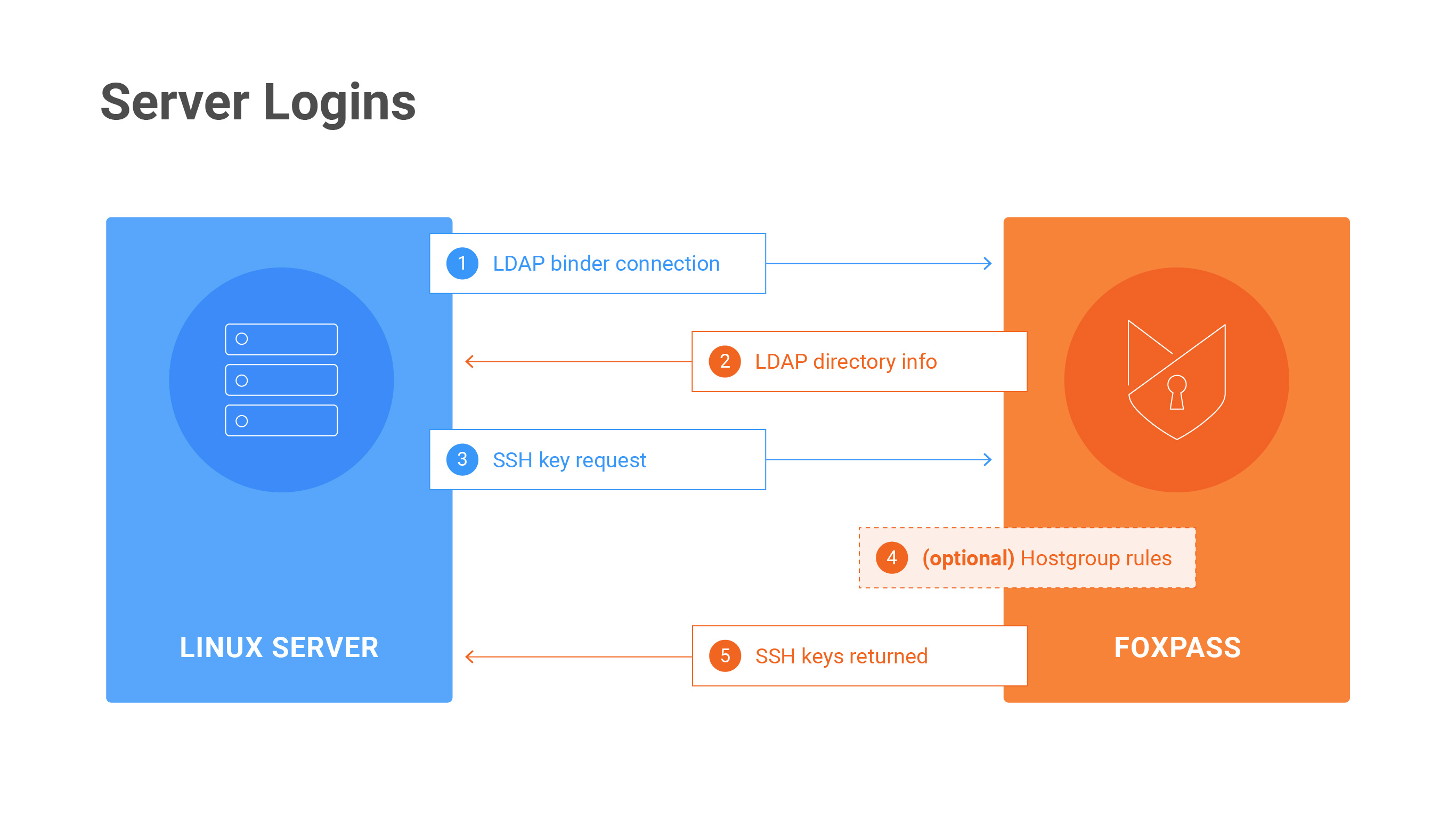
Server Login Diagram
Can't log in to the instance once Foxpass is enabled? Try these steps:
1. Check the LDAP logs
Check the LDAP logs in Foxpass here:
https://console.foxpass.com/settings/ldaplogs/
This will show you any attempted connections to our LDAP server as well as the status of the connection attempt. If you don't see any expected requests, then something is probably misconfigured between your server and Foxpass (ex. bad host name, invalid binder name, bad Foxpass port). If you're seeing successes but still not getting access, something is probably misconfigured on your host.
2. Is it just this user?
If it's just one user having trouble, check to see:
a) If this user has a 'local' account (look in /etc/passwd). If so, the SSH keys script won't ask the Foxpass server for their keys.
b) If this user is not in the appropriate host groups in the Foxpass console.
3. Can this instance talk to our LDAP service?
Run these commands:
getent passwd
getent groupUsers (or groups) pulled from Foxpass should be at the end. Do you see any?
If not, check the following logs for errors:
- syslog (/var/log/syslog)
- sssd (/var/log/sssd.log)
- nslcd logs
Common issues:
a) Firewall rules preventing connection to ldap.foxpass.com port 636
b) Wrong bind username/password
c) Wrong base DN
Does this all look good? then ...
4. Try to get public SSH keys returned for your user
Run this command:
sudo /usr/local/sbin/foxpass_ssh_keys.sh <username>(note, on some machines this file will be in /usr/local/sbin/ or elsewhere)
Do you get any keys to print to standard out?
If yes, then contact our support. Something beyond the scope of this document is going wrong.
If no keys are retured, check:
- Is the user enabled as an "Engineering" user in Foxpass?
- Does this user have any keys uploaded to Foxpass?
- Do you have port 443 access to api.foxpass.com?
If none of those are the issue and you're not getting keys returned, then ...
5. SELinux might be doing its job
If you have SELinux enabled (common with CentOS, RedHat), sshd might be unable to call 'curl' and fetch users' keys. In this case regular LDAP commands like 'getent passwd' and 'getent groups' would still work, but logging in via SSH key or running the SSH key script would fail.
You can have two options to get around SELinux restrictions, you can either disable SELinux entirely or selectively grant Foxpass permissions. First you should check the audit log after an SSH key request to make sure that SELinux is actually blocking it. Then, run the grep command below and check the output.
grep "denied" /var/log/audit/audit.logIf SELinux is blocking Foxpass, you should see lines that contain comm="curl" or comm="foxpass_ssh_key".
Disable SELinux Entirely
This is useful to get things working quickly, but may not be the best way to manage your security long term. To disable SELIinux, open /etc/selinux/config and set SELINUX=disabled. Then restart the host for the settings to take effect:
shutdown -r nowAfter the host restarts, log in and run sestatus to check the status of SELinux. It should say 'disabled.' Now, the Foxpass SSH key script and your SSH based logins should work as normal.
Grant Foxpass Minimal Permissions
SELinux has tools that can automatically compile necessary permissions to unblock an application. However, these tools can only see the permissions missing from the most recent request, so you may have to run the tools multiple times to grant deeper levels of permissions. Generally, SELinux blocks the 'curl' and 'foxpass_ssh_key' commands.
To grant Foxpass appropriate permissions, you'll need to repeat this process as necessary.
- Generate an SSH key request. This can be done by attempting to log in to the host with an SSH key or running the get SSH key script using the command /usr/local/bin/foxpass_ssh_keys.sh<username>.
- Check the audit logs. Run the grep command above. Check the timestamps to make sure that the denials line up with your most recent request. Make note of what commands (the variable inside comm="
<command>") SELinux is blocking. - Grant the commands SELinux permissions. Run the two lines below as necessary for each command. The first line creates a file for SELinux to parse, and the second line loads the file into SELinux. Samples have been provided for granting curl or foxpass_ssh_key permissions as well as for generic commands. For each subsequent run, increase the trailing number to your .pp file.
ausearch -c 'curl' --raw | audit2allow -M my-curl-1
semodule -i my-curl-1.ppausearch -c 'foxpass_ssh_key' --raw | audit2allow -M foxpass-ssh-1
semodule -i foxpass-ssh-1.ppausearch -c 'foxpass_ssh_key' --raw | audit2allow -M foxpass-ssh-1
semodule -i foxpass-ssh-1.ppRepeat these steps as necessary until your SSH login succeeds or the SSH key script runs successfully.
Updated 4 months ago
