Integrating Yubikey with Foxpass
If you are using pam_yubico in Amazon Linux 2023 here is the separated guide for it.
To get the server to prompt for and validate a code from the default Yubicloud service on Ubuntu 16.
Note that to log in, type your password followed by pressing the Yubikey button. pam_yubico.so will remove the OTP from the password string, leaving the prefixing bytes for pam_ldap.so to use.
1. Configure Foxpass LDAP on Your Host
Configure Foxpass on your Linux host using the appropriate instructions. Instructions are listed in the "Linux configuration" section on the left. Make sure to note the LDAP binder and password you use during setup, as you will need it later.
2. Install the Yubico Package
Install the libpam-yubico package on the host using the following command:
apt-get install libpam-yubico3. Edit the Yubikey Configuration
Open the /etc/pam.d/common-auth file with a text editor and edit the "pam_yubico.so" line like so:
# lines above
# then the pam_yubico line, like so
auth required pam_yubico.so mode=client id=<YUBICLOUD_ID> key=<YUBICLOUD_KEY> ldap_uri=ldaps://ldap.foxpass.com ldapdn=ou=people,dc=example,dc=com user_attr=uid yubi_attr=yubikey_id ldap_bind_user=cn=binder,dc=example,dc=com ldap_bind_password=<FOXPASS_BIND_PW>
# this line is already in your common-auth file
auth required pam_ldap.so minimum_uid=1000 use_first_pass
# ... might be more below ...YUBICLOUD_ID and YUBICLOUD_KEY can be generated at https://upgrade.yubico.com/getapikey/.
ldapdn is ou=people + your base Foxpass DN.
yubikey_id is a custom user field you set in Foxpass. Enable custom fields from the 'Configuration' page and set the user's keys individually on the 'Users' page or using the /users/:username/ API call.
ldap_bind_user is the full name of the LDAP binder you used in Step 1.
ldap_bind_password is the password to the LDAP binder you used in Step 1.
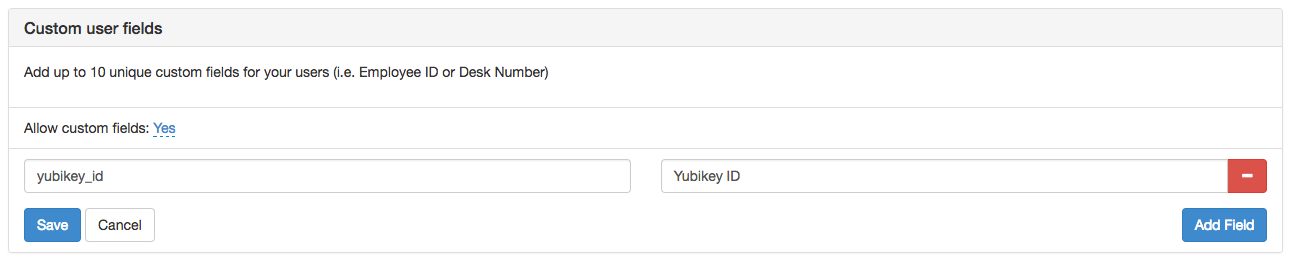
Configuration screenshot
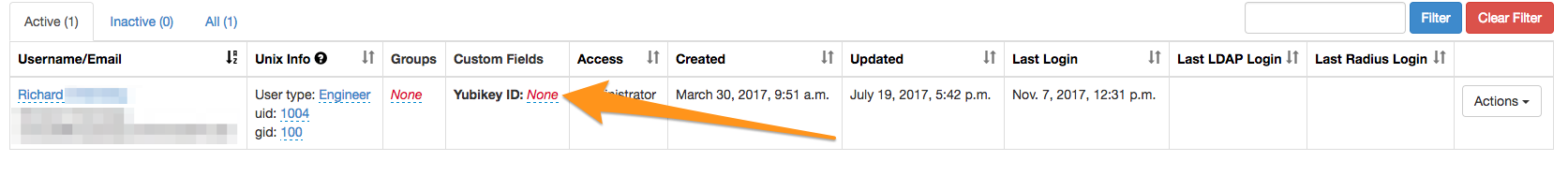
User screenshot
4. Edit the SSH Configuration
Open the /etc/ssh/sshd_config file with a text editor and add this line to the bottom of the file:
AuthenticationMethods publickey,passwordThis will make the server use an interactive prompt for Yubikey authentication. Note: Additional configuration is needed to make this work for non-interactive users.
5. Add Yubikey ID for each user
Go the the users page in Foxpass, and set the user's Yubikey ID to the first 12 characters of their OTP.
Updated 3 months ago
