EAP-TLS MDM setup
This guide outlines the steps to configure a secure wireless network connection using Extensible Authentication Protocol-Transport Layer Security (EAP-TLS) for mobile devices managed through Mobile Device Management (MDM) systems like Apple Configurator, Workspace one, JAMF Pro, JAMF School, Intune, etc. EAP-TLS is a highly secure protocol that uses certificate-based authentication to ensure data integrity and confidentiality.
Simple Certificate Enrollment Protocol (SCEP) allows your devices to easily enroll for a certificate using our SCEP endpoint and perform other Public Key Infrastructure (PKI) related operations. We currently issue certificates with a validity period of 5 years so that you don't have to worry about renewing your certificate every year.
Configure EAP-TLS on Foxpass
Please follow the EAP-TLS initial setup guide to create client CA, server CA and SCEP endpoint if not configured already.
Creating Endpoints for SCEP enrollment
Make sure you have our Advanced RADIUS add-on enabled for your account to access this feature. In our system, you have the flexibility to create endpoints tailored to different verification types. These verification types can include users, devices, or even a scenario where no specific verification is required. Below are the options available for endpoint creation:
- General Endpoints for MDMs (Mobile Device Management)
- Dedicated Endpoints for Intune
Create SCEP endpoint for MDMs
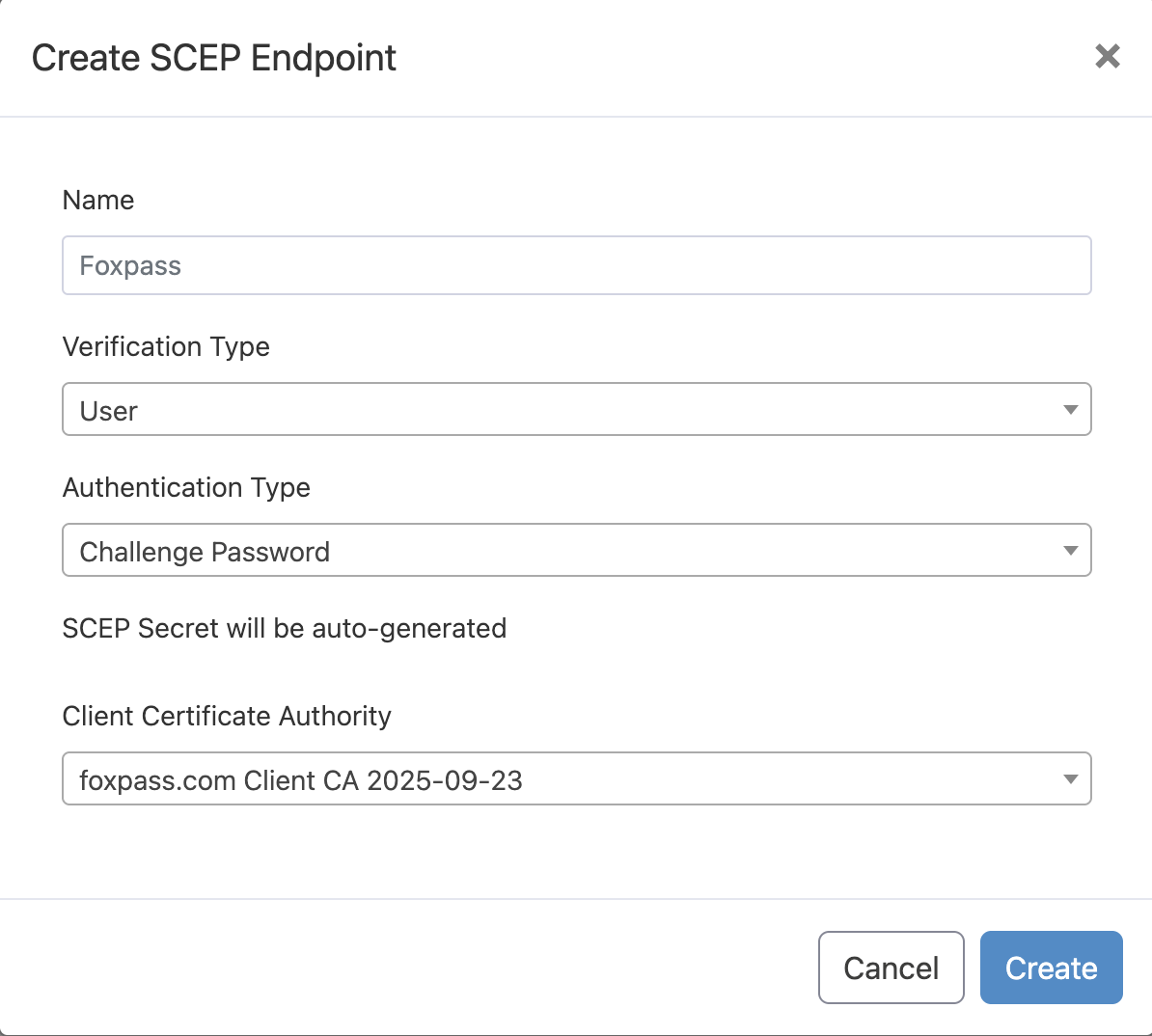
- Click on Create SCEP endpoint button on the SCEP page.
- Give a name to your endpoint say 'Foxpass'.
- Depending on your use case, select verification type as User, Device or None (see Choosing Verification type at the end of this page).
- Authentication Type - Challenge Password.
- Client Certificate Authority - Created in the EAP-TLS Initial setup guide here.
- Click 'Create' button.
Create SCEP endpoint
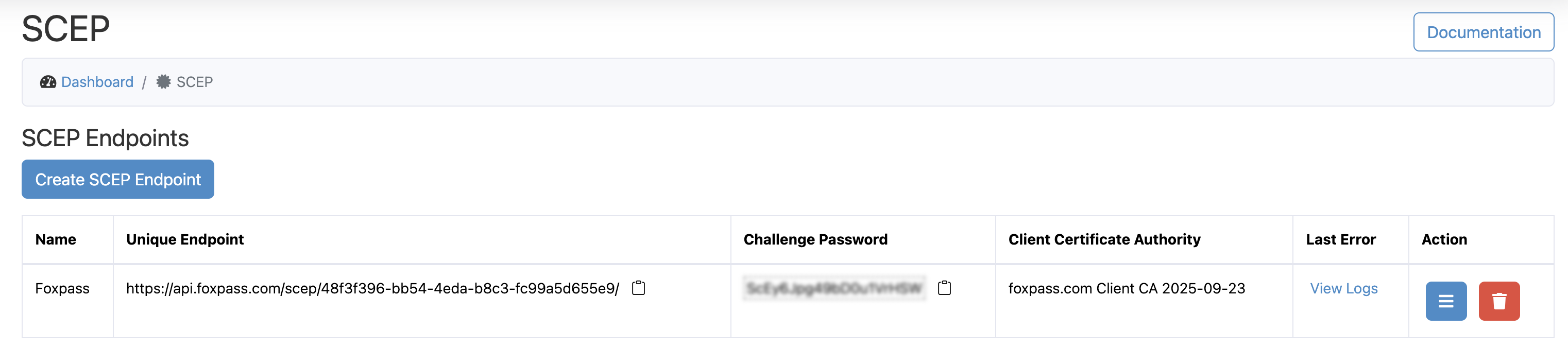
You will be able to see your new endpoint with challenge password.
Sample SCEP endpoint
Create SCEP endpoint for Intune
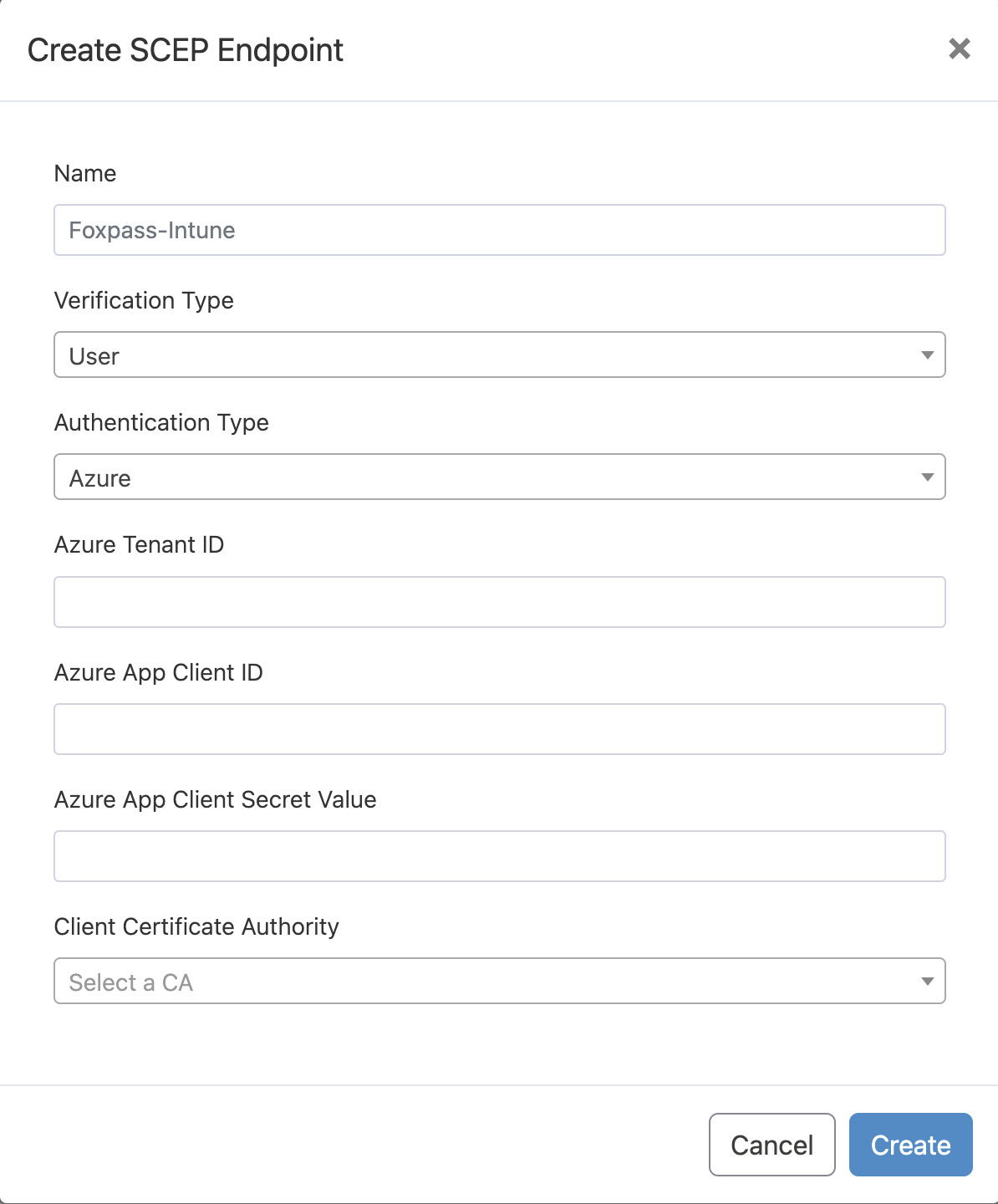
- Click on Create SCEP endpoint button on the SCEP page.
- Give a name to your endpoint say 'Foxpass-Intune'.
- Depending on your use case, select verification type as User, Device or None (see Choosing Verification type at the end of this page).
- Authentication Type - Azure.
- For Azure Tenant ID, Client ID and Client secret please refer this documentation.
- Client Certificate Authority - Created in the EAP-TLS Initial setup guide here.
- Click 'Create' button.
Create SCEP endpoint for Intune
Choosing Verification type
The "verification" field on the SCEP endpoint can User, Device, or None.
- If it's set to "User", then the SCEP certificate request must include a valid, enabled user's email address as the Subject (CN), or as the SAN - rfc822 field. Furthermore, when a device attempts to connect to RADIUS, we'll verify the user's email is still in the list of enabled Foxpass users.
- If it's set to "Device", then the SCEP certificate's CN field must equal a device's UDID as it appears on the device page . We can syncronize devices from Azure, Google, and Jamf. If you have another MDM, then we cannot syncronize device records so you will have to use "Verification" = None (below). Furthermore, when a device attempts to connect to RADIUS, we'll verify the device UDID is still in the synchronized list.
- A Verification type set to None allows you to create certificates with any Subject (CN). Furthermore, if any SCEP endpoint has "Verification" set to "None", then matching a user or device during a RADIUS request is optional. A match will still be attempted, though, in order to apply Group conditional attribute rules.
Updated 4 months ago
