RADIUS Overview & Debugging
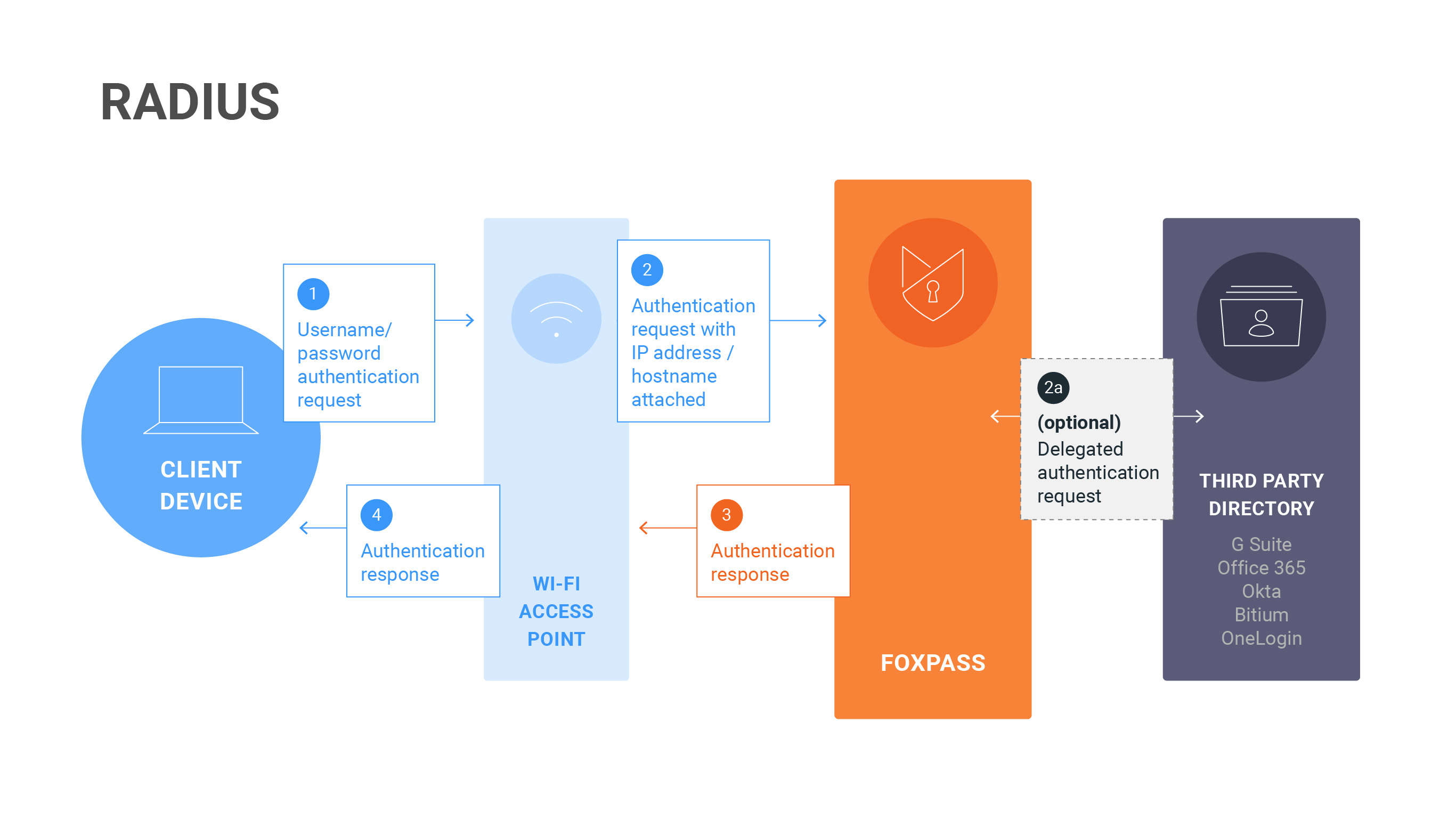
RADIUS Diagram
Sometimes, we might not have detailed instructions for your specific RADIUS integration. We've provided here a generalized set of instructions for configuring an RADIUS integration and debugging any potential problems.
RADIUS Basics
RADIUS is a protocol commonly used for authenticating users onto a local network or VPN. Without RADIUS, users log into a Wi-Fi network using a shared password. With RADIUS, they log into the network using an individual username and password. Additionally, RADIUS can send custom response attributes for each user to segment them on a particular sub-network and separate their traffic.
One tricky thing about RADIUS is that it can utilize multiple different types of protocols to connect. While the flexibility can be helpful, some of these protocols have been exploited and are now considered insecure. If you'd like to read more on the topic, check out our explainer: Is RADIUS secure?.
Configuring the Connection
Most RADIUS setups will follow a similar pattern. First, you'll create a RADIUS Client to register your endpoint with Foxpass. Then, you'll configure your access point, switch, or VPN with your RADIUS Secret and specific Foxpass attributes. You'll also configure any RADIUS attributes or VLAN settings in Foxpass, if necessary. Finally, you'll configure your phones, computers, and other devices to connect to RADIUS using the appropriate protocol.
We recommend that customers utilize multiple Foxpass IPs for their Access Point configuration. That way the Access Point can use a fallback in case the first one is unreachable. The IP addresses for your account can be found on the RADIUS Settings page in Foxpass.
What are the different types of RADIUS authentication methods?
In addition to the protocols listed in our explainer, we also support PAP-Hybrid authentication via a wired connection. This allows you to whitelist devices using their unique MAC address, bypassing user and password authentication. This is especially useful for devices like printers or VOIP phones.
RADIUS Restrictions & Common Pitfalls
As noted above, certain RADIUS protocols are considered insecure and are disabled by default. However, we will enable them on a case-by-case basis if you understand the security risk and contact us. Do note that enabling these protocols may require your users to reset their passwords or to disable delegated authentication.
Many Access Points and other integrations offer the ability to test your connection after setting it up. However, those connection tests often use an insecure protocol to connect to Foxpass so the connection is rejected. However, regular user logins using the correct configuration will work as expected.
For Apple devices running macOS and iOS you'll need to install a special .mobileconfig file to connect to Foxpass. First, you'll specify the Wi-Fi network name in Foxpass. Then you'll download and install the file on your device. However, those devices can struggle when you change your password. Currently, these devices assume your password is still correct and silently retry the authentication, blaming network errors when authentication continues to fail. This can be particularly troublesome when you have a lockout policy for authentication attempts. You can avoid this behavior by forgetting and re-adding the network or removing and re-adding the profile after changing your password. This behavior can change with OS updates, so we can't guarantee you'll have the same experience across all your devices.
Debugging & Troubleshooting
Your basic debugging process will go something like this:
- Test the connection. Try logging into your network or VPN. This will generate a request from your application to Foxpass.
- Check our RADIUS logs. If you don't see the request in the RADIUS logs, then there's something wrong with your configuration. Double check that your configuration is correct and test the connection again. If you do see the request, check to see what the error is.
- Check your password. Make sure that you're using the correct password. We'll note in the logs what data source we are checking against as to whether it's local (Foxpass) or remote (Third Party).
OS-Specific tools
- Windows: Windows WLAN debugging
Updated 3 months ago
