Okta / Foxpass password delegation
Password Delegation for RADIUS is not compatible with PEAP. You must use EAP-TTLS-PAP (preferred) or PAP.
Password Delegation for RADIUS is not compatible with PEAP. You must use EAP-TTLS-PAP (preferred) or PAP.
This describes how to set up Foxpass to delegate password verification to Okta.
1. Create a new Okta user
Go to "Admin", then "Directory", then "Add Person". Add a user named "Foxpass"
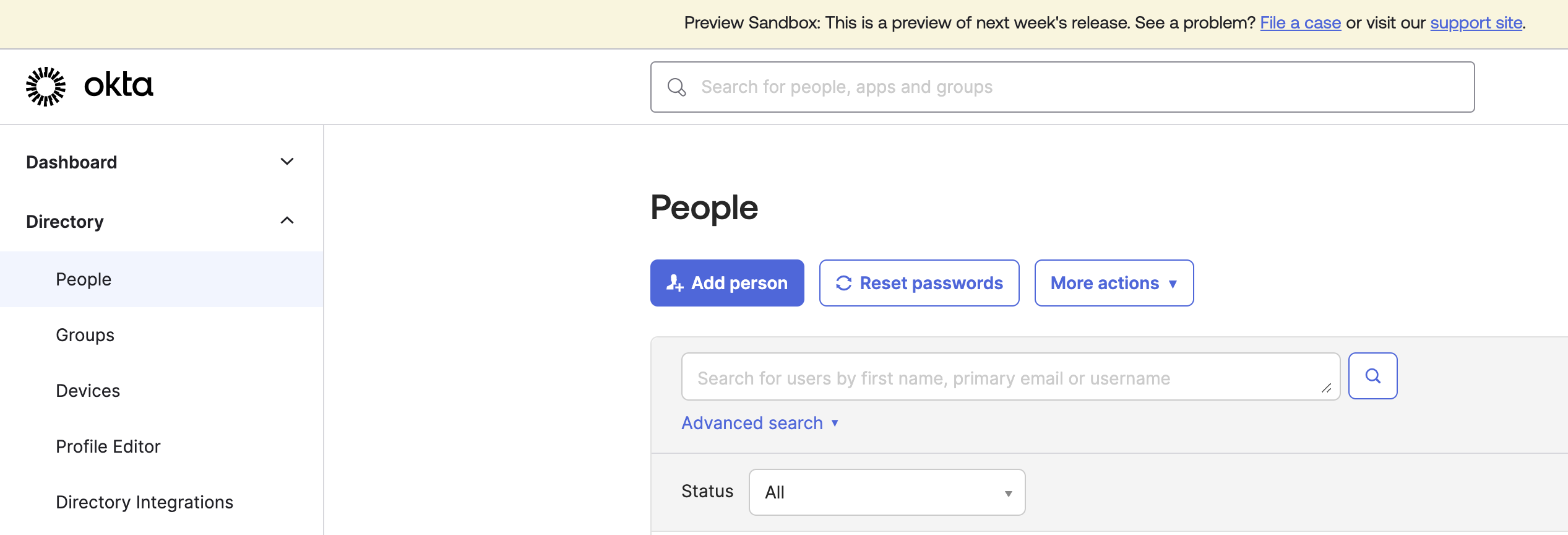
Add Person
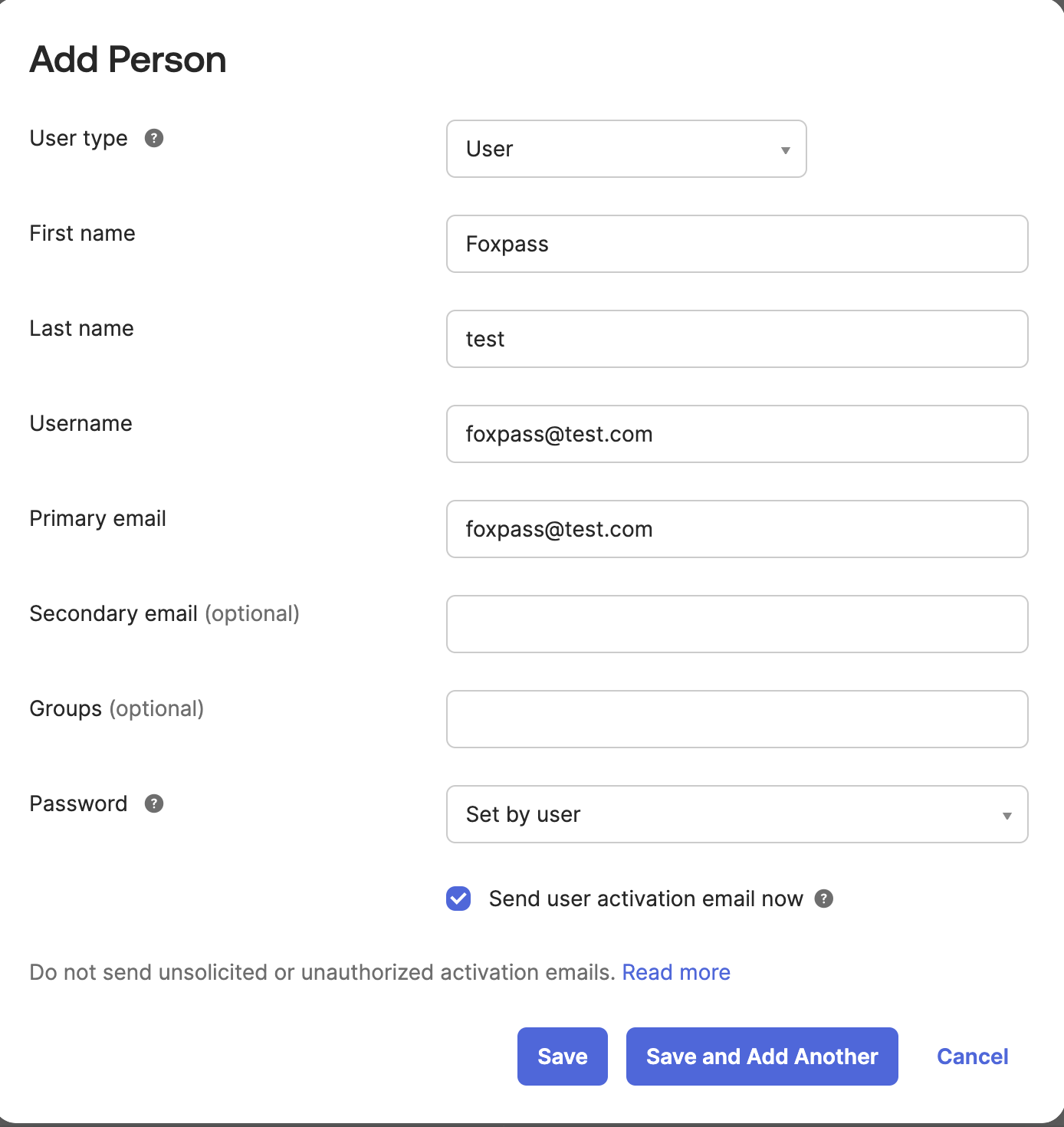
Add user "Foxpass"
2. Make that user an admin
Go to "Admin", then "Security", then "Administrators". Give the "Foxpass" user Read-Only Admin rights. If you would like to keep 2FA on for requests from Foxpass, give the user Group Admin rights instead.
3. Get that user's API key
Log into Okta as the Foxpass user we created in step 1. Generate an API key using the instructions from Create an API Token.
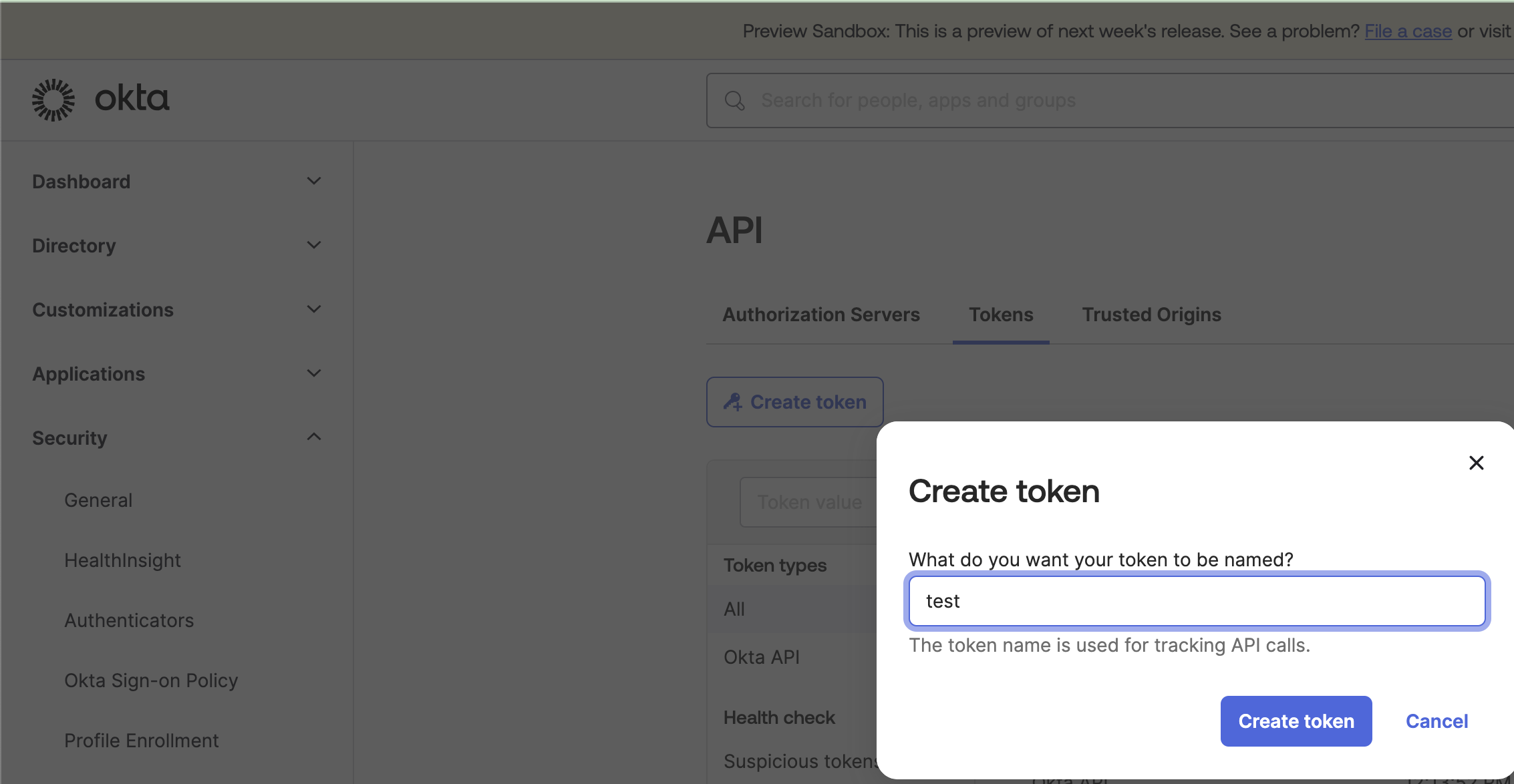
Create API Token
4. Put that API key into Foxpass
Go to the Foxpass 'Auth Settings' page. Go to 'Delegate authentication to' and choose 'Okta' from the dropdown.
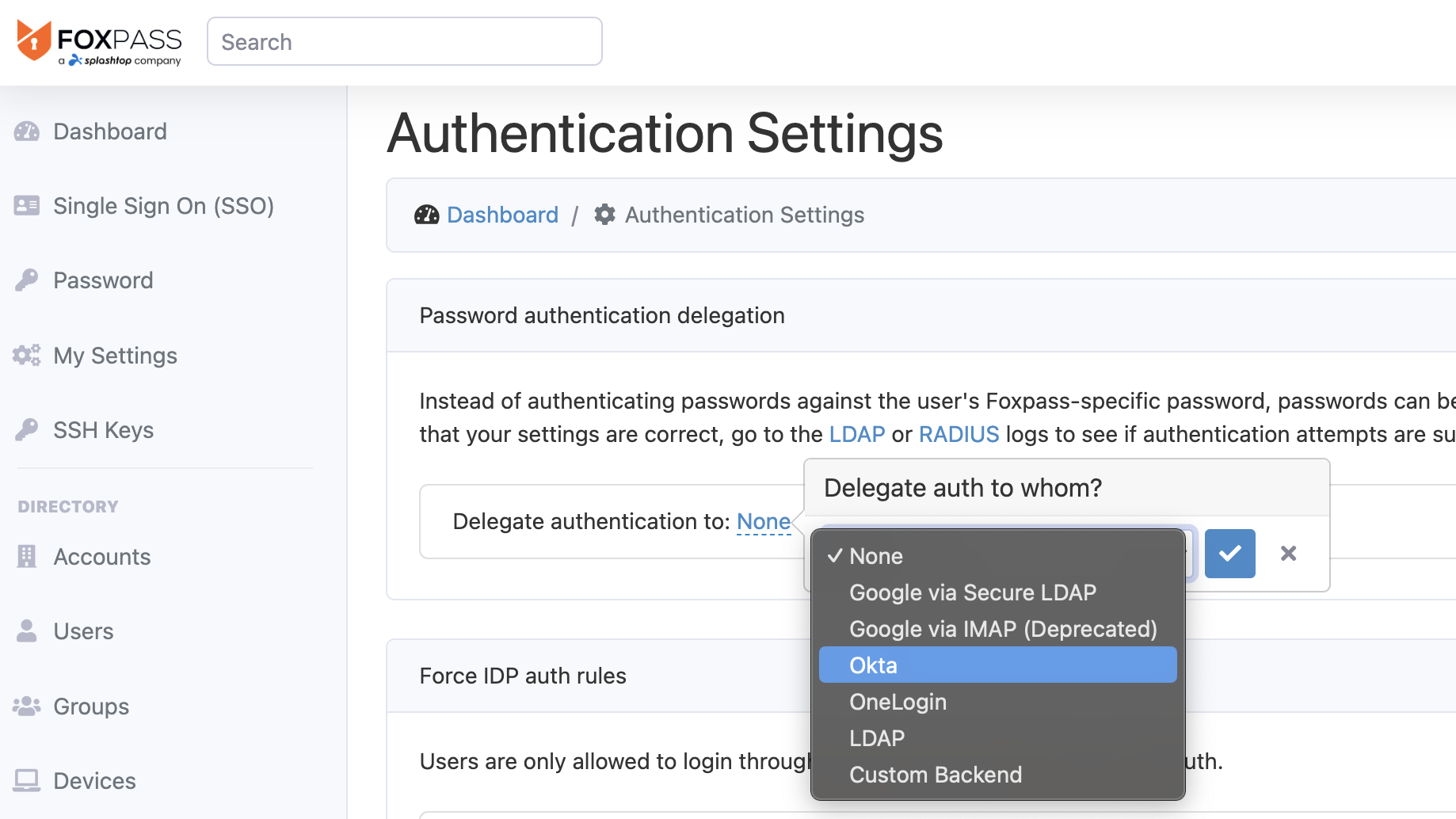
Choose 'Okta'
Enter your Okta site's URL and the API key you generated above.
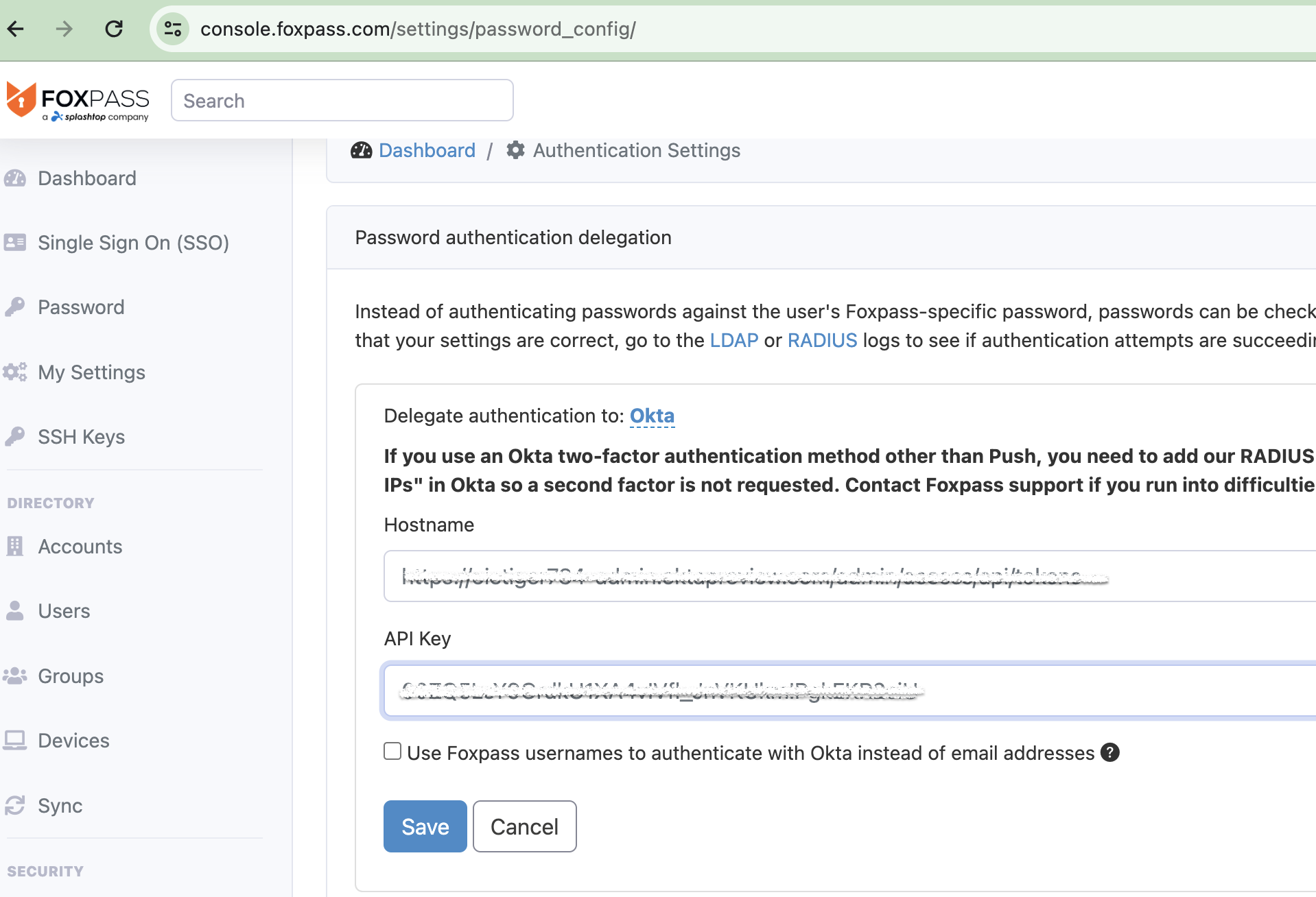
Enter Okta site's Hostname and API Key
5. Add 2-factor exemption
Okta's two-factor is compatible with Foxpass's LDAP interface. If you plan to use Foxpass's Cloud RADIUS interfaces, then using 2FA is not recommended because users will be prompted to verify 2FA at least every hour, and possibly every time the user connects to a new access point. As for LDAP, bypassing MFA may be desired depending on how you're integrating Foxpass with your application.
To disable Okta's MFA you need to add our outbound IP addresses to be "in-zone" in Okta.
First, go to the Networks page under the Security header in the admin interface. Create a zone to include our outbound IP addressees (below).
For the IP addresses for delegated authentication, see:
Delegated Authentication IP Addresses
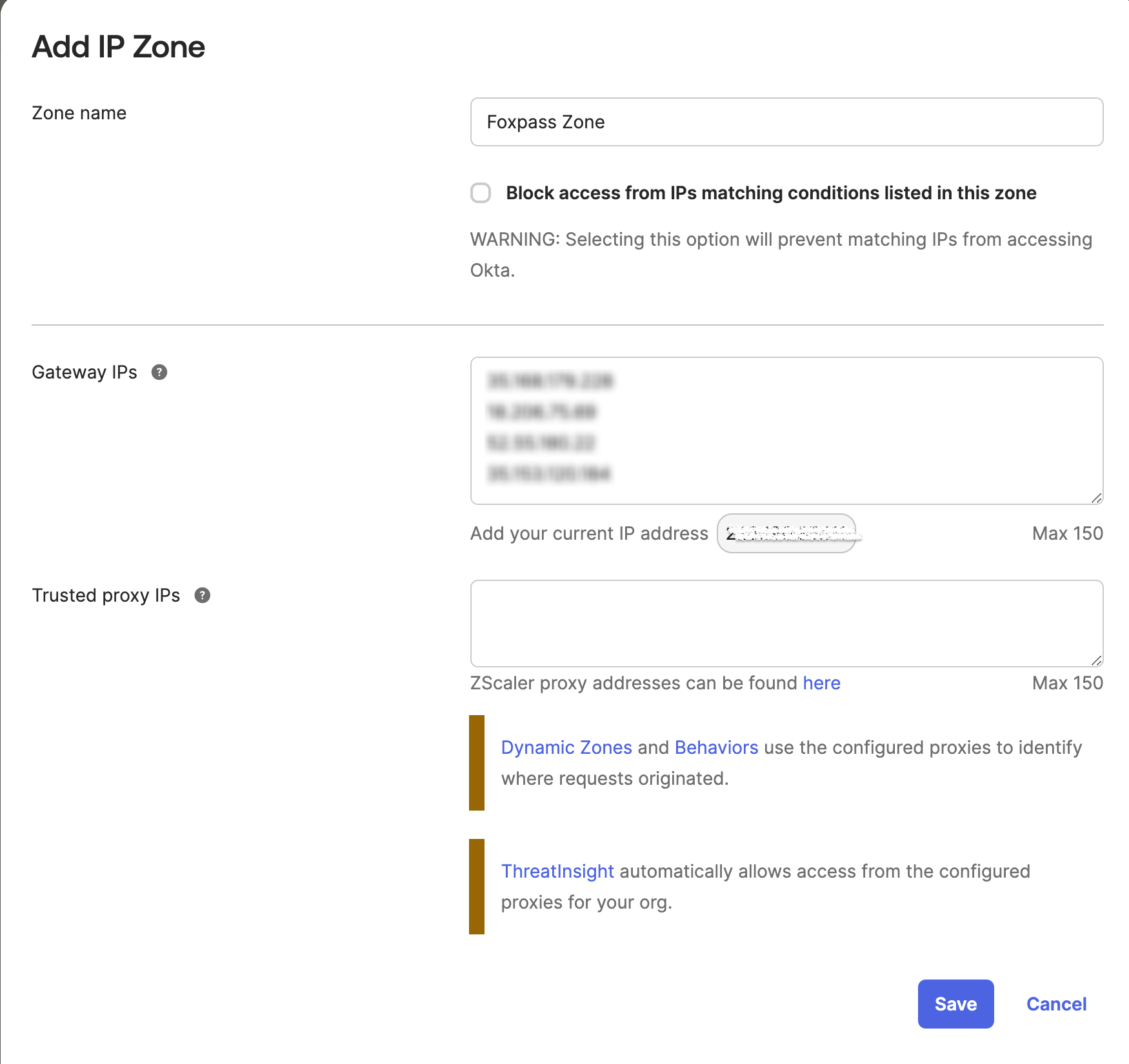
Add IP zone
Then, go to the Authentication section under the Security header and select the Okta Sign On Policy tab. Now, add an exemption to any two-factor policy the IP zone you used previously. You can do this by selecting your MFA rule and setting "IF User's IP is: Not In Zone" and selecting the zone you added Foxpass's IP's to. Then you're all good to go!
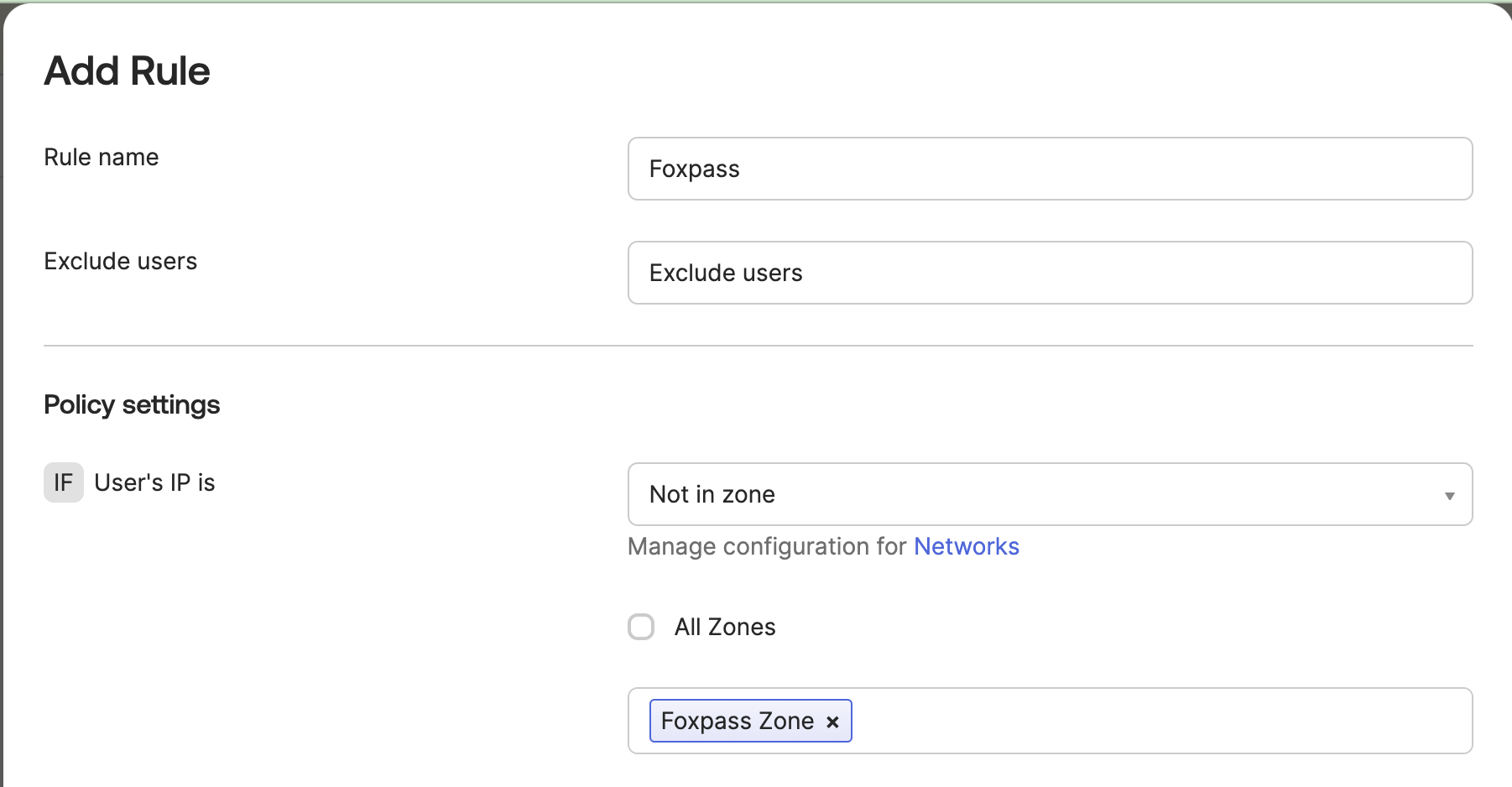
Add exemption
6. Add ThreatInsight exemption
Include the zone you created in step 5, above, as an "exempt zone". See example screenshot, below.
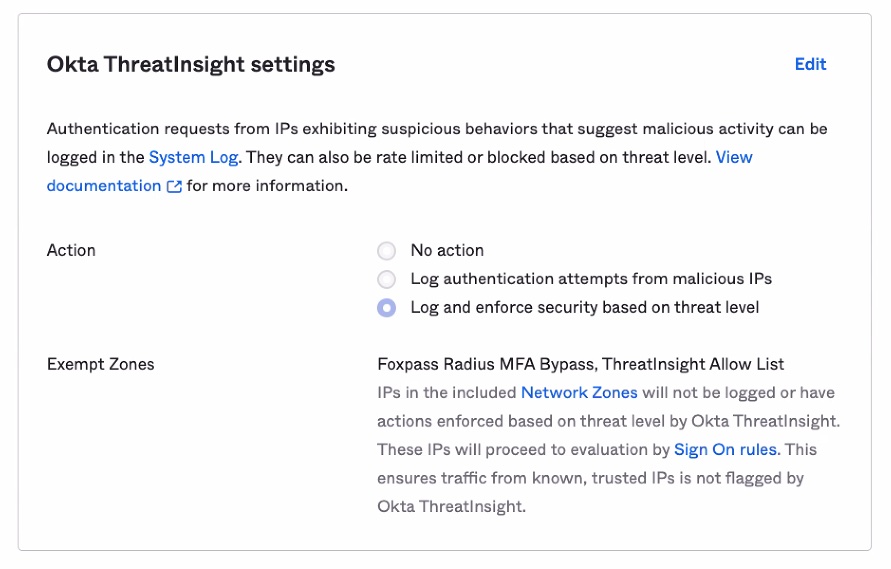
Add threatinsight exemption
Updated 3 months ago
