EAP-TLS - Initial setup
First time setup on EAP-TLS page
This guide tells you the one time set up for Foxpass in order to use MDM's like Apple configurator, JAMF etc. Make sure you have our Advanced RADIUS add-on enabled for your account.
Download Client CA
- Go to the Foxpass EAP-TLS page. Click on Create new CA button under 'Client Certificate Authorities'.
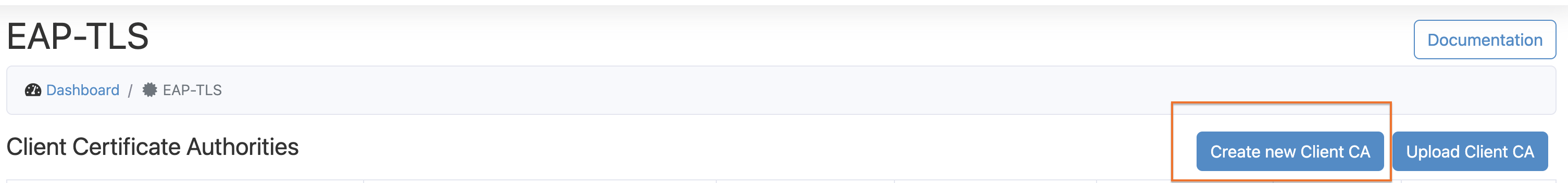
Click Create new Client CA
- Edit CA name, CA validity and Certificate Validity Period if desired.
- Click 'Create CA' button.
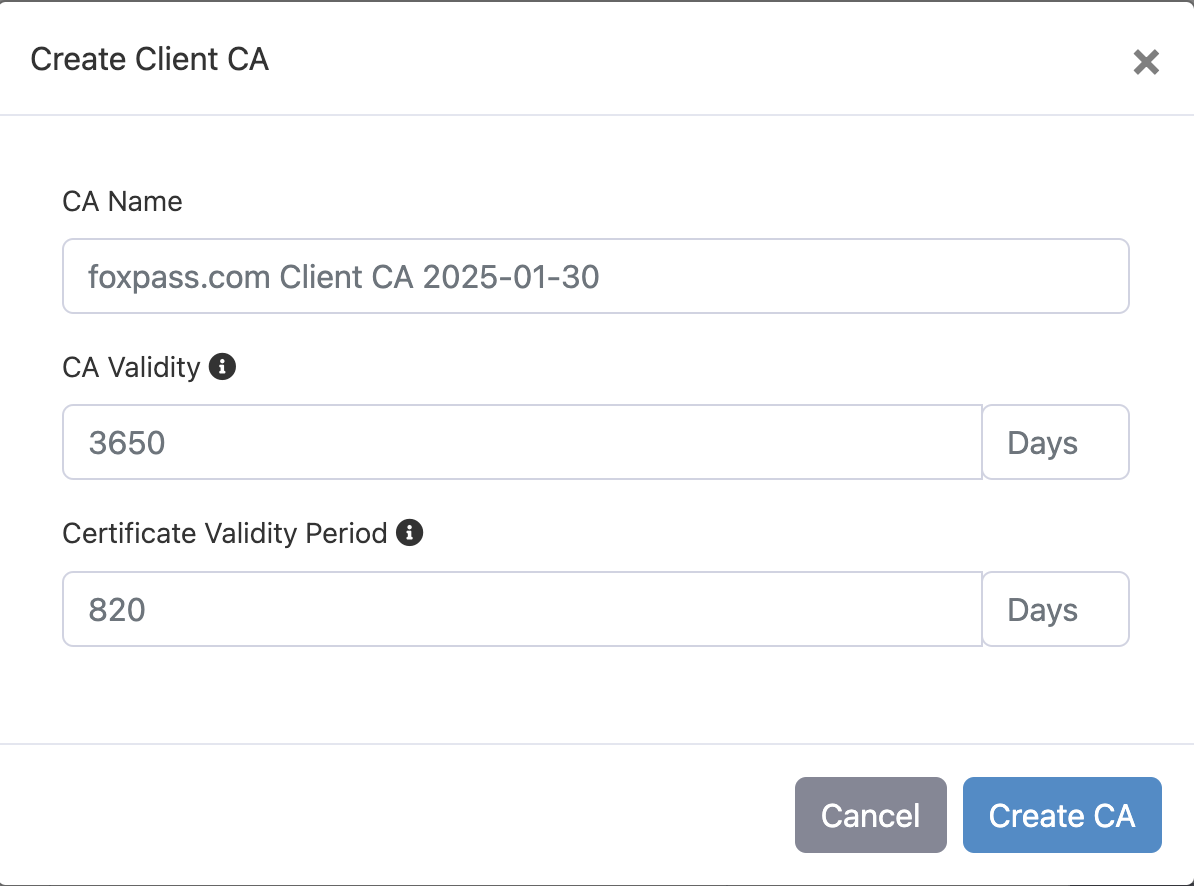
Create CA
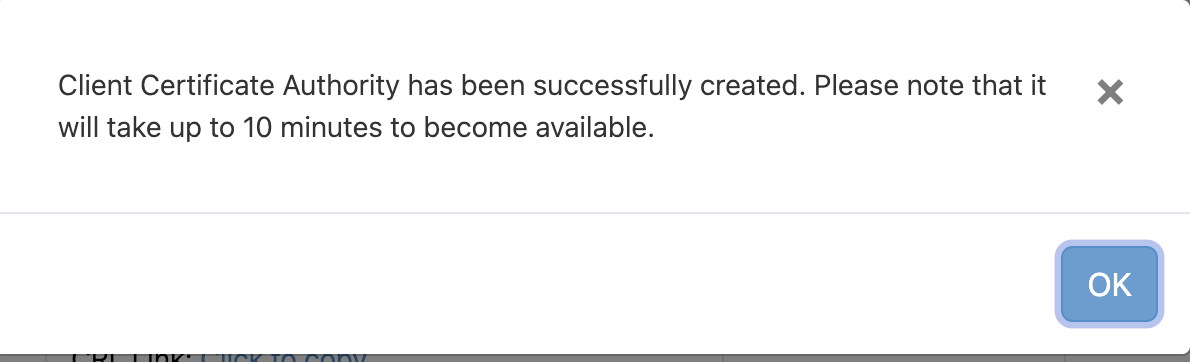
Click Ok
Click on 'Download CA' button. The CA can be used later in setting configuration files for MDM.
Download Server CA
Click on Create new Server CA under 'Server Certificate Authorities'. You will see a dialog box saying that 'Server Certificate Authority has been successfully created.'
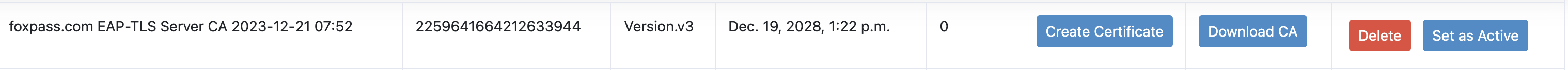
Server CA created
Now click on 'Create certificate' and then 'Set as Active'.
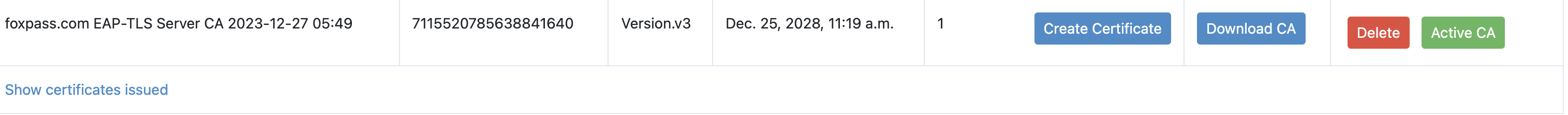
Server CA marked as active
Click on 'Download CA' button. The CA can be used later in setting configuration files for MDM.
Configure SCEP Endpoint
You can create a SCEP endpoint with Verification Type as User or Device or None depending on your requirement. For MDM's like Apple configurator, JAMF etc you will need to configure Authentication Type as 'Challenge Password' and for Azure authentication type as 'Azure'. You can choose verification type as user, device or None depending on your use case.
Authentication Type : Challenge Password
Option 1: User certificate
- Go to the SCEP page on Foxpass.
- Click 'Create SCEP endpoint' button.
- Name - < Your choice>
- Verification Type: User
- Authentication Type: Challenge Password
- Client Certificate Authority: Select the client CA created earlier.
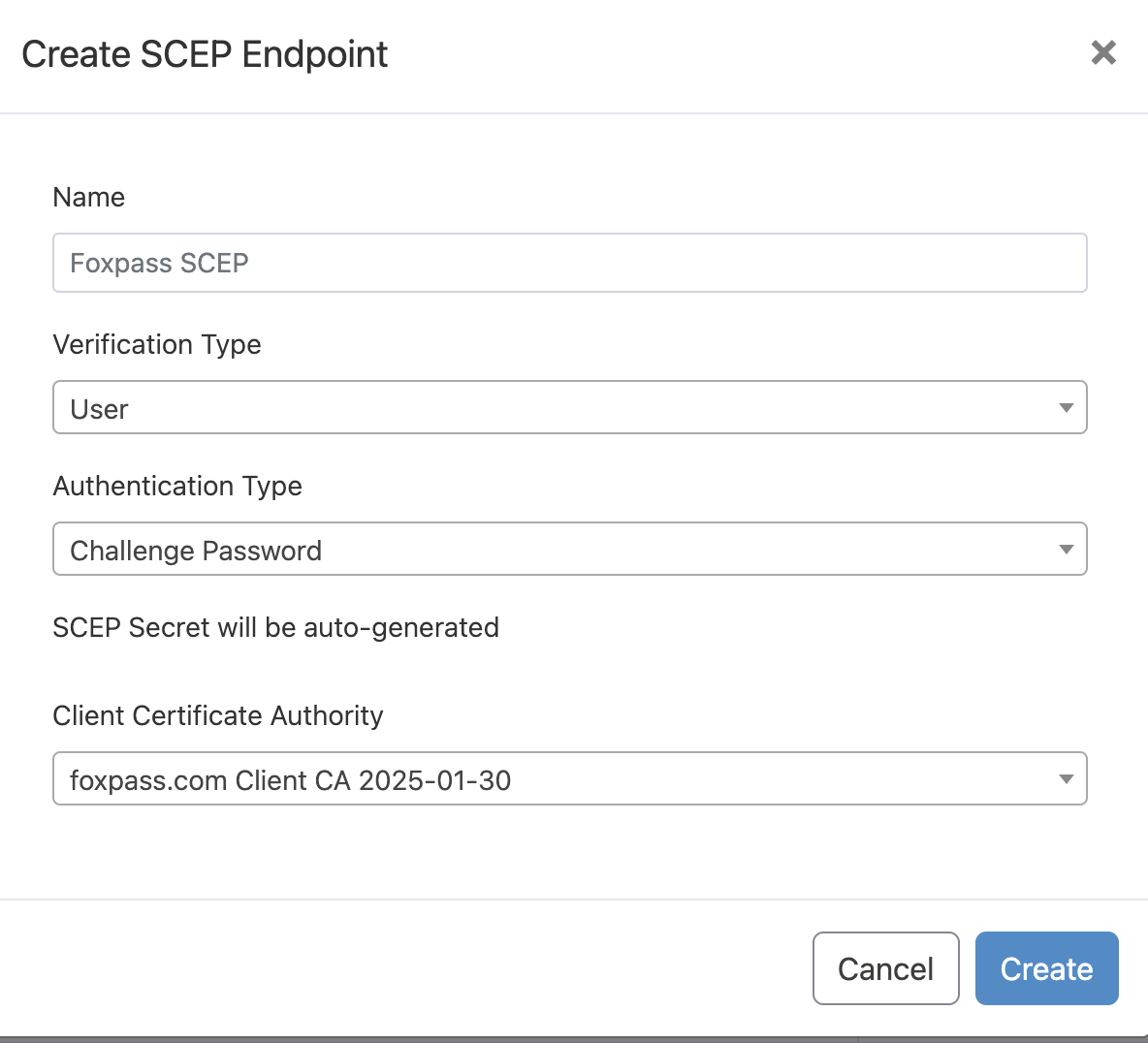
SCEP endpoint - User certificate and challenge password
Option 2: Device certificate
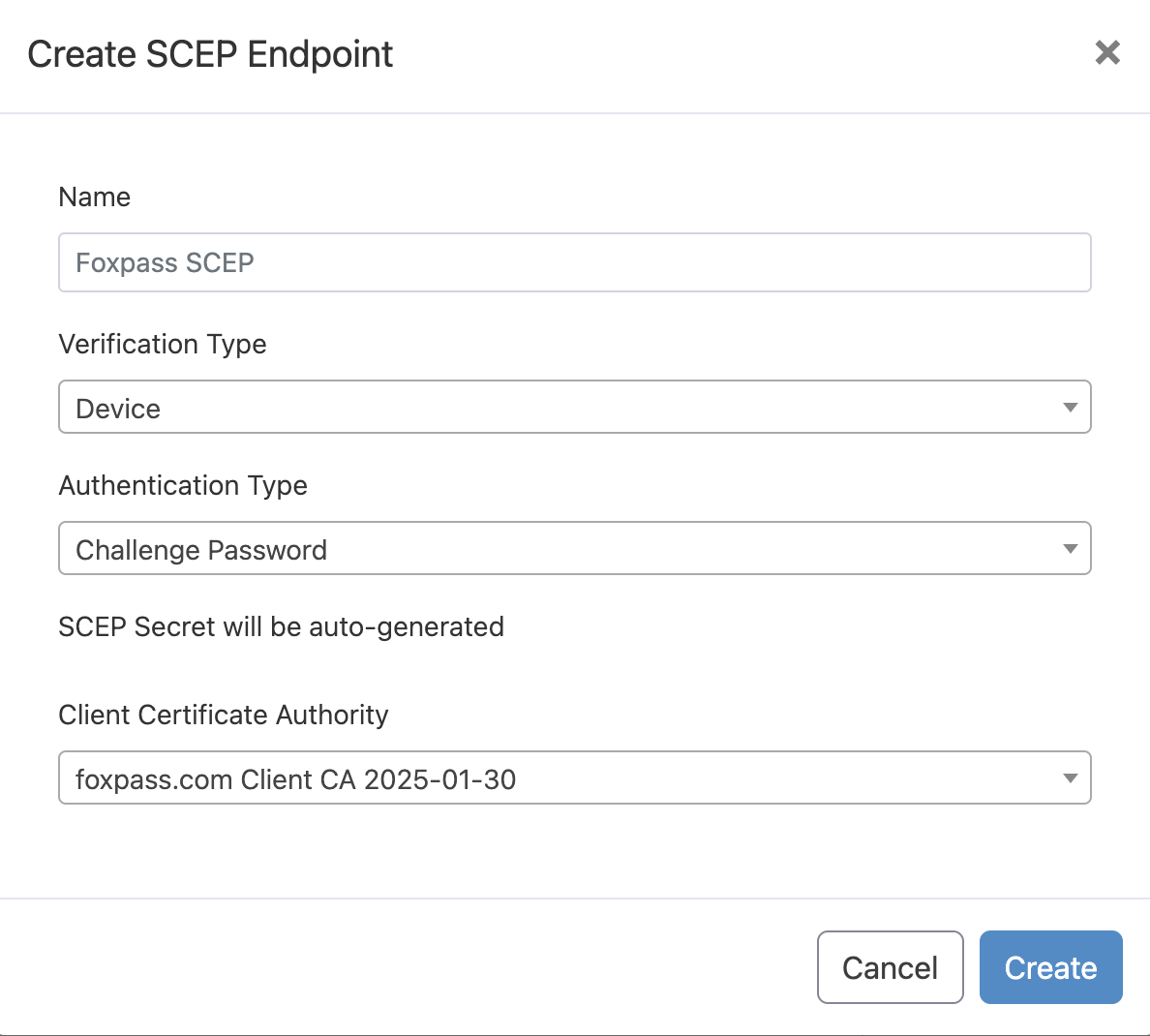
SCEP endpoint - Device certificate and challenge password
Choose 'None' for verification type if you don't want to verify whether it is device or a user certificate.
Authentication Type : Azure
Option 1: User certificate
- Name - Give a name to your endpoint.
- Verification type - User
- Authentication type = 'Azure'
- Azure Tenant ID - Paste the Tenant ID copied from Azure. Refer Intune Initial Setup documentation for the respective values.
- Azure Client ID - Paste the Client ID copied from Azure
- Azure app client secret - Paste the secret copied from Azure
- Click 'Create' button.
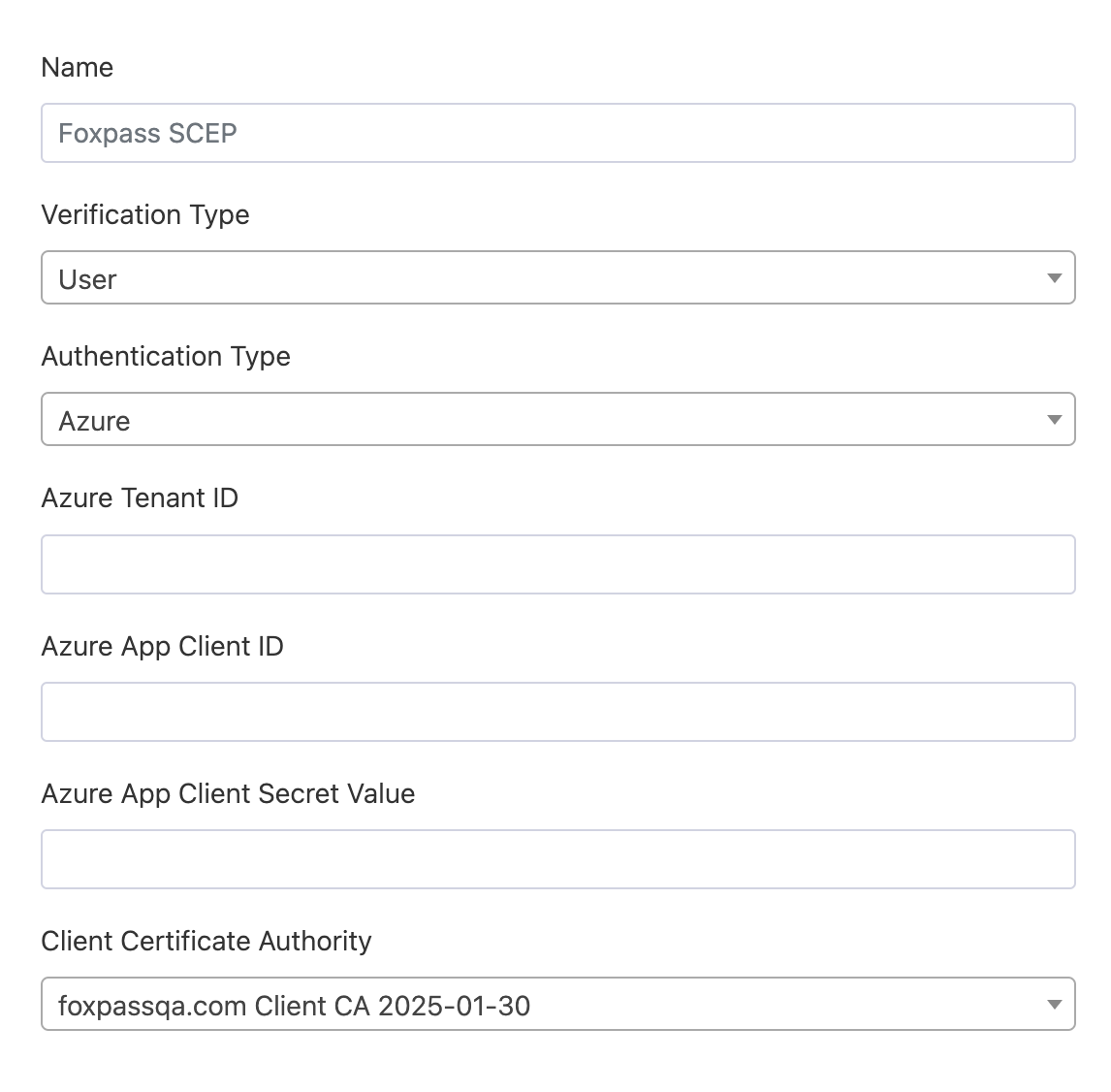
User certificate and Azure authentication type
Authentication Type : Azure
Option 2: Device certificate
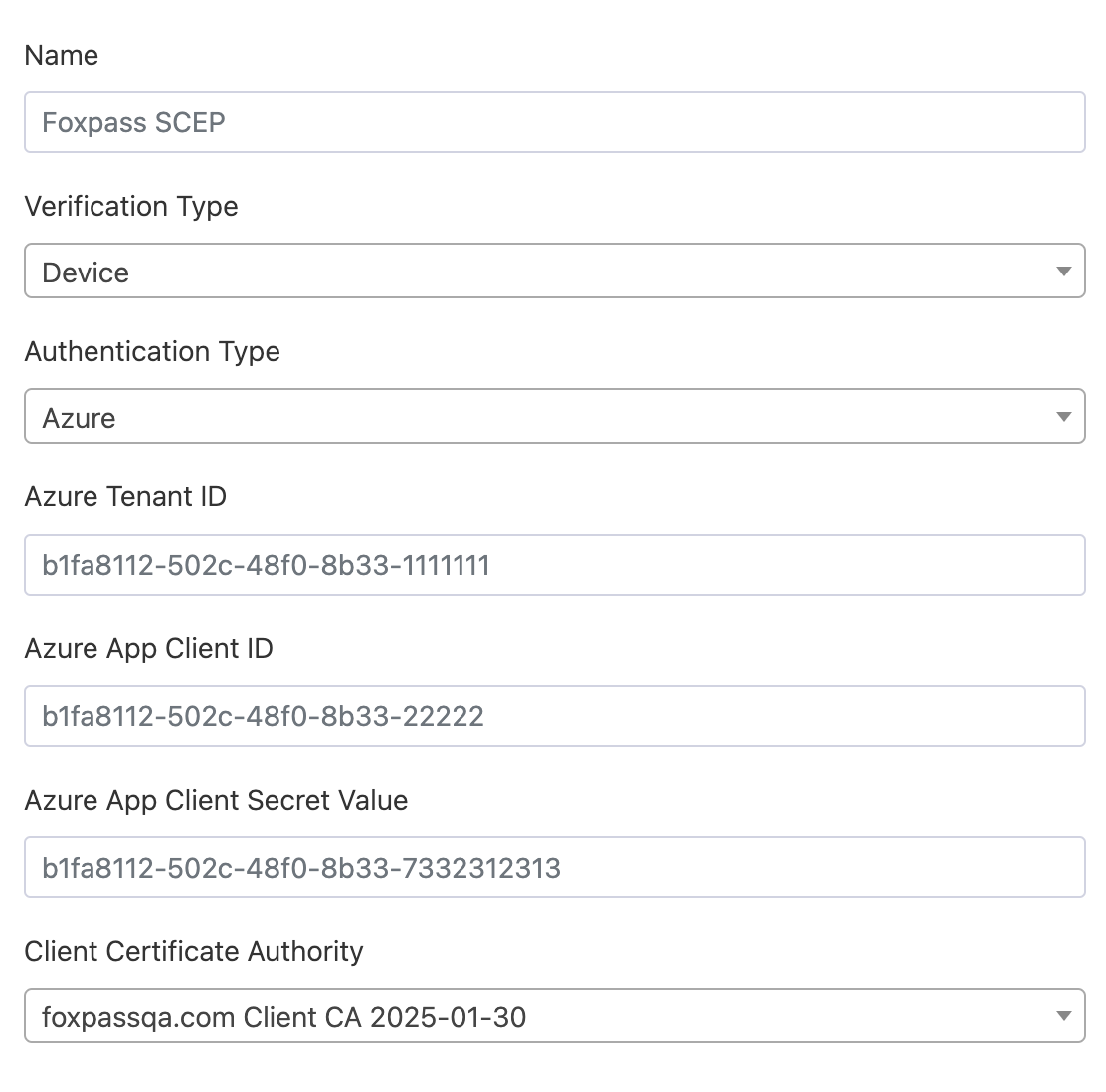
Device certificate and Azure authentication type
Once the SCEP endpoint is created, note the unique endpoint and challenge password. You will need it while configuring MDM's.
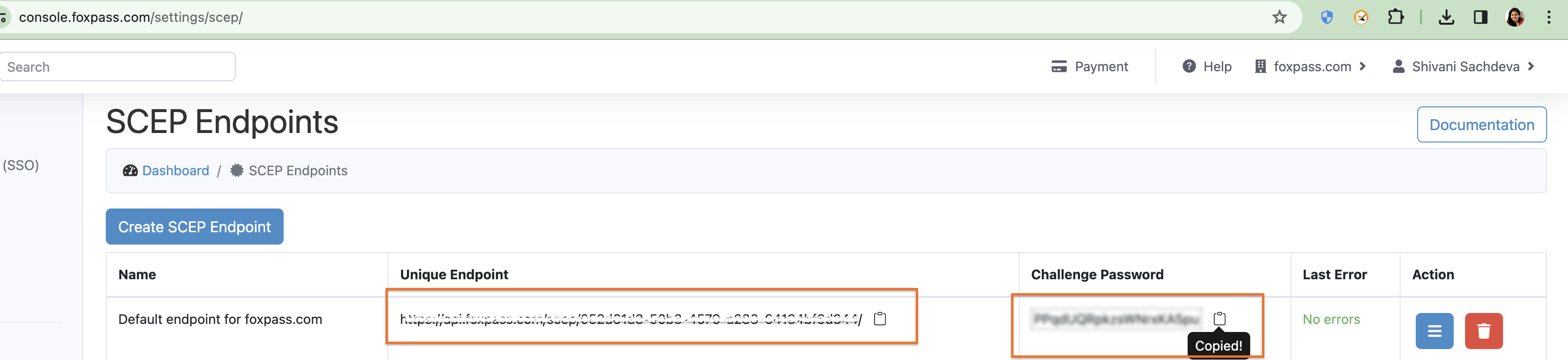
Note SCEP URL and Challenge password from the SCEP page
Certificate listing and revocation
The Foxpass Console's EAP-TLS lists all your issued certificates along with their serial, information, status, issue, and expiry date. You can revoke a certificate by selecting a valid reason.
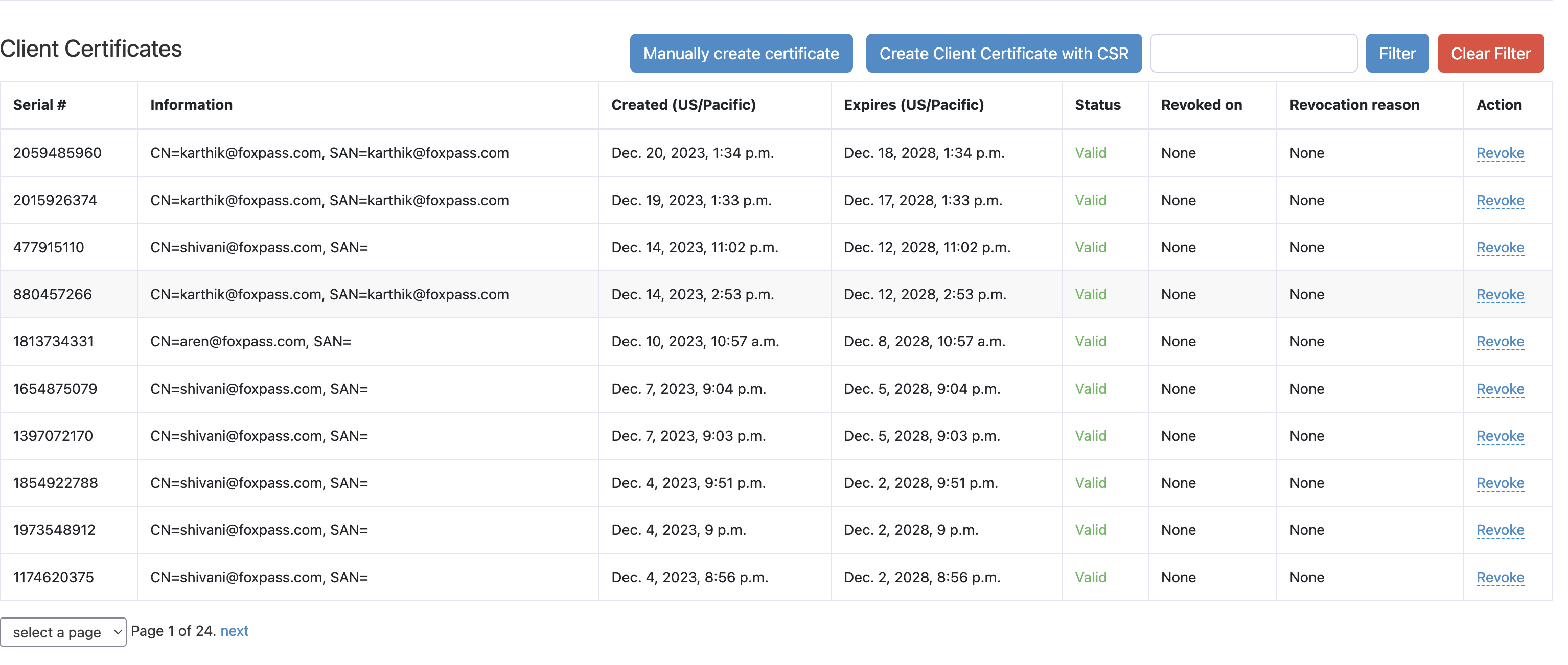
Client certificates
Please see the section to your left for various MDM's documentations.
Updated 4 months ago
