Foxpass RADIUS Proxy
Foxpass RADIUS proxy is NOT for network (e.g. Wi-Fi) access.Wireless (and wired) access uses EAP, and the RADIUS proxy does not supports EAP. EAP connections use EAP-TTLS, EAP-TLS, or PEAP and are already secured by an embedded stream that uses the TLS protocol.
Network authentication must connect directly to one of our cloud-RADIUS servers.
Executive Summary
The Foxpass RADIUS Proxy securely forwards RADIUS PAP authentication requests from internal devices to Foxpass servers over HTTPS.
It protects sensitive credentials by tunneling legacy authentication protocols through secure web traffic without requiring major infrastructure upgrades.
Full setup and technical implementation instructions are available on the Foxpass RADIUS Proxy GitHub repository.
Overview
The Foxpass RADIUS Proxy is a lightweight server application that enhances the security of legacy RADIUS clients.
It encrypts otherwise vulnerable PAP authentication requests and safely forwards them to Foxpass cloud servers using HTTPS.
This proxy enables organizations to securely use Foxpass with devices that support only basic RADIUS functionality.
Why Use the Proxy?
• Protects against the security risks of transmitting PAP authentication directly over the Internet.
• Provides secure communication between legacy network devices and Foxpass cloud services.
• Seamlessly integrates with existing firewalls, VPNs, and network appliances that rely on PAP authentication.
Devices that supportRadSec (RADIUS over TLS) can connect directly to Foxpass without requiring the proxy.
How It Works
- Internal VPN, firewall, or network devices send PAP-based RADIUS authentication requests to the local RADIUS Proxy server.
- The proxy securely encrypts and forwards the requests to Foxpass servers over HTTPS.
- Foxpass validates the credentials against internal or delegated identity sources.
- Authentication responses (success or failure) are sent back to the proxy, which then returns the corresponding RADIUS response to the originating device.
Architecture Overview
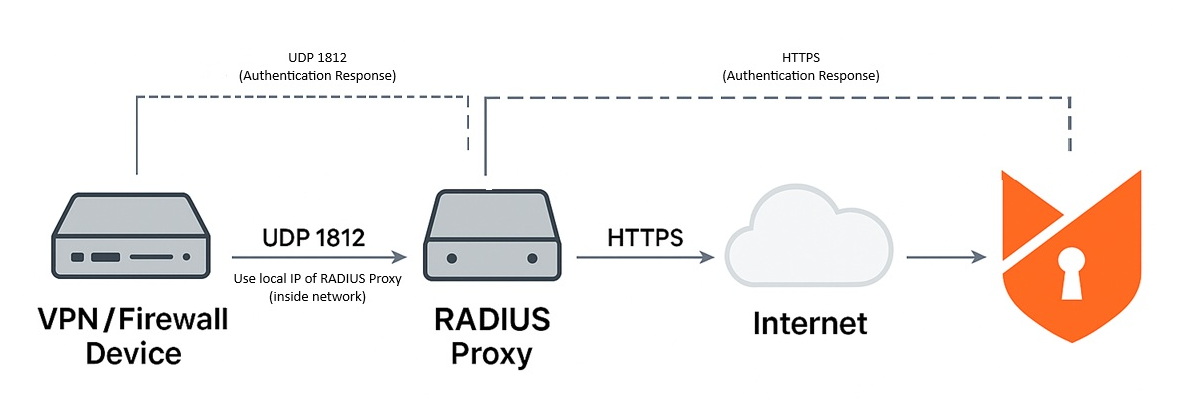
Secure Authentication Flow Using Foxpass RADIUS Proxy
• Internal RADIUS traffic remains protected inside the local network.
• Sensitive credentials are secured through HTTPS during Internet transmission.
• Foxpass handles all authentication validation securely.
Requirements
• A local server (e.g., Linux VM, Raspberry Pi) with Python 3 installed to run the RADIUS Proxy.
• Outbound HTTPS (TCP port 443) access from the proxy to api.foxpass.com.
• Network devices (firewalls, VPNs, switches) configured to use PAP authentication.
Setup Instructions
For installation and configuration instructions, please refer to the Foxpass RADIUS Proxy GitHub Repository
Updated 4 months ago
