Azure AD/Entra ID Foxpass password delegation
Password Delegation for RADIUS is not compatible with PEAP. You must use EAP-TTLS-PAP (preferred) or PAP.
This describes how to set up Foxpass to delegate password verification to Azure AD/Entra ID.
Set Azure AD/Entra ID as your Delegated Authentication type
Go to the Foxpass 'Auth Settings' page. Scroll down to "Password authentication delegation." Choose Azure/Office 365 via OAuth from the dropdown menu and click "Save." 2FA must be turned off or Foxpass IP's must be marked as trusted in your MFA configuration. If 2FA needs to be enabled for a specific user or set of users, you can exempt them from delegated authentication and they can use a Foxpass password instead.
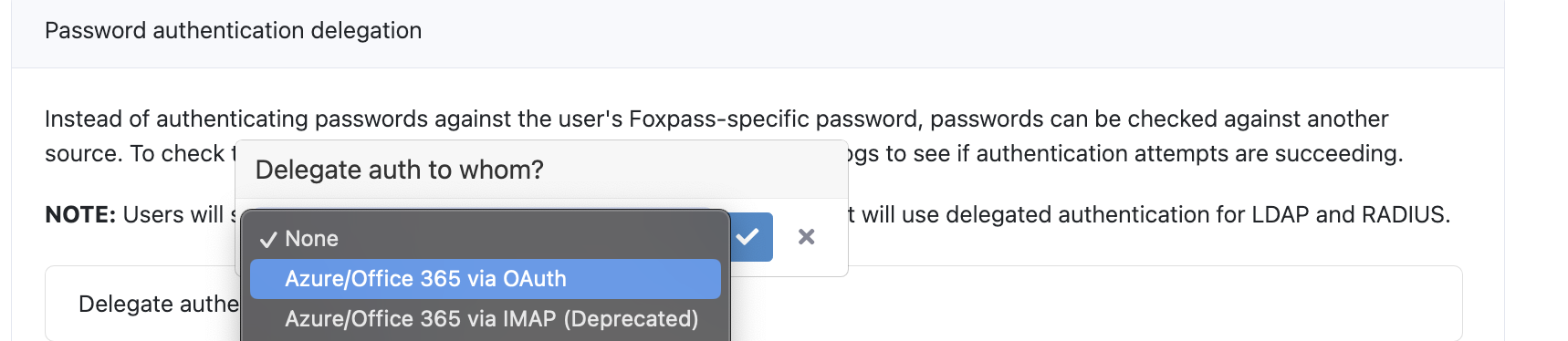
Set Azure/Office 365 as delegate authentication
If you use Azure Conditional Access Policies, please use the Advanced instructions below.
Note: Select the Azure/Office 365 via OAuth optionAzure's IMAP endpoint is deprecated. Please see here for more information.
Basic Instructions: Setting Up MFA Trusted IP's
Due to a limitation in Azure's authentication endpoints, users cannot have Azure's MFA turned on and enable delegated authentication. We recommend keeping MFA enabled and marking Foxpass IP's as trusted. Marking Foxpass's IP's as trusted allows us to check usernames and passwords while bypassing MFA. To read more about Azure trusted IP's, read here:
https://docs.microsoft.com/en-us/azure/multi-factor-authentication/multi-factor-authentication-whats-next#trusted-ips
To mark our IP's as trusted, go to the Azure Active Directory portal at https://aad.portal.azure.com/. Then, go to the Named Locations section. You should see a link to Configure MFA Trusted IP's.
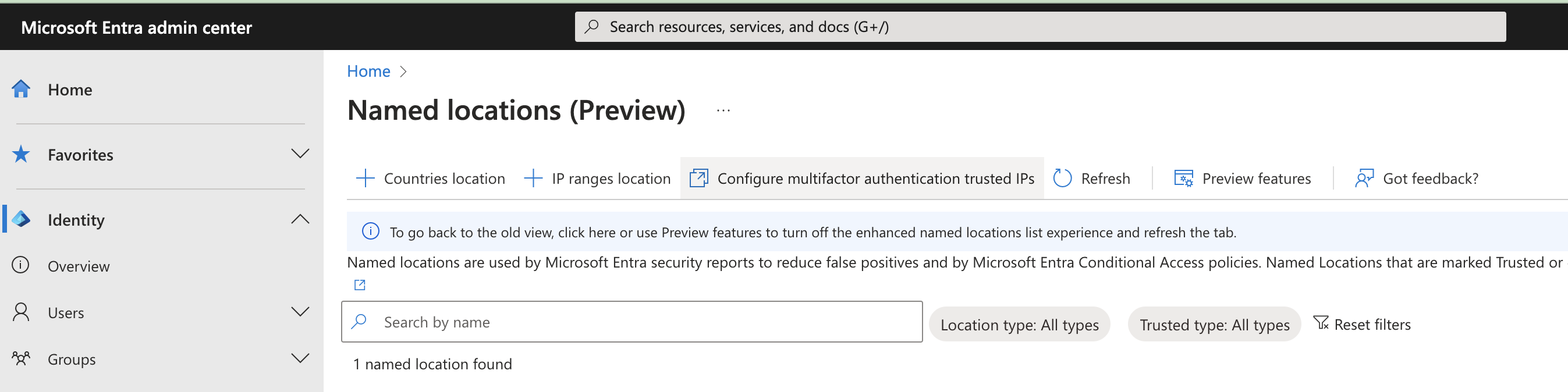
Configure MFA trusted Ip's
You can now enter Foxpass's IP's in the field. If you'd rather have your users use an application specific passwords, you can enable that setting here as well.
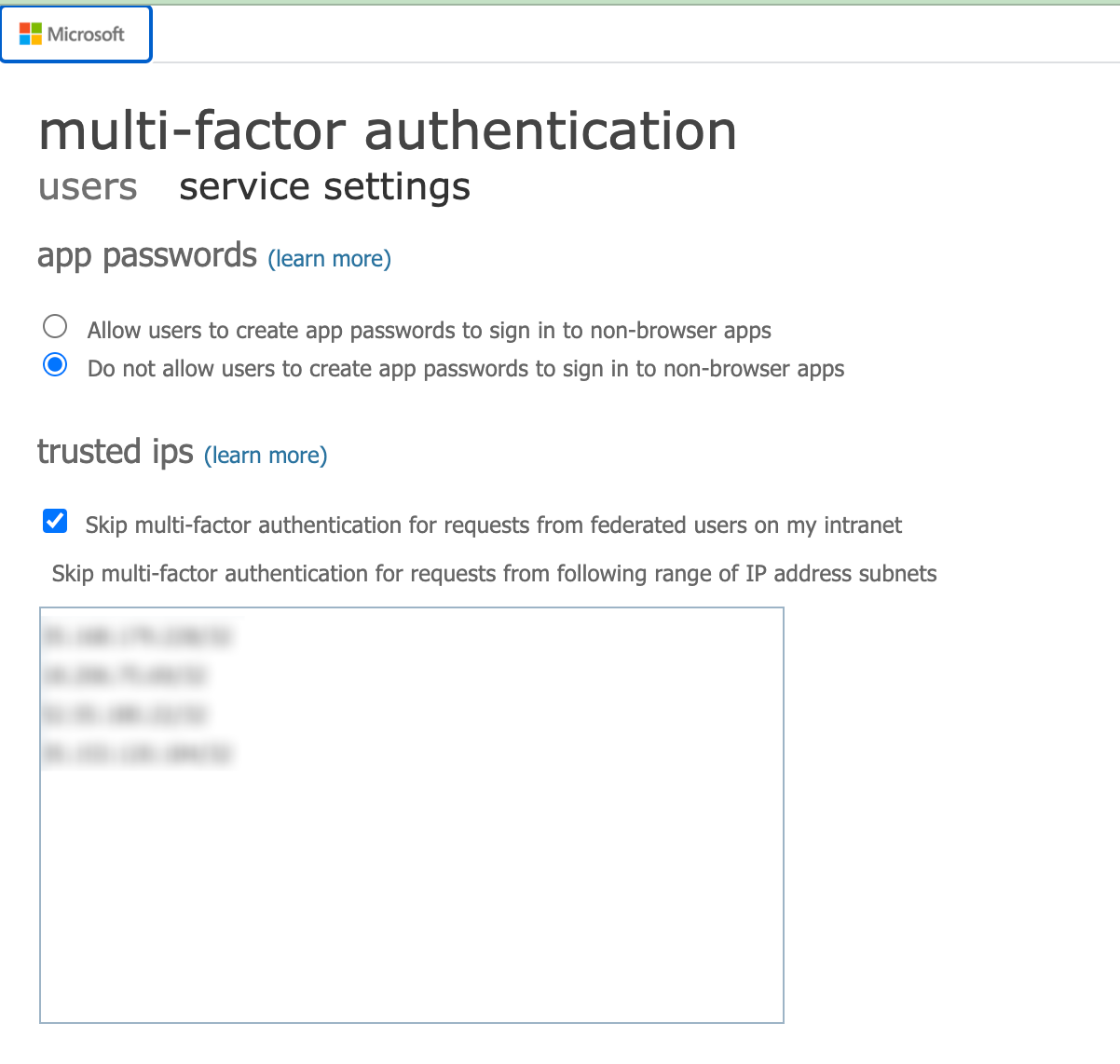
Enter Foxpass IP's
To get the IP addresses for delegated authentication, please see:
Delegated Authentication IP Addresses
Advanced Instructions: Azure Conditional Access Policies
If you have Azure Conditional Access policies enabled, make sure that they allow requests from Foxpass's servers. You may need to set up a named location for Foxpass or further configure your policies.
First, go to the Azure Active Directory admin center for your organization. Select All Services from the left hand menu and find Azure AD Named Locations. Create a new IP ranges location named Foxpass with the above listed IP addresses.
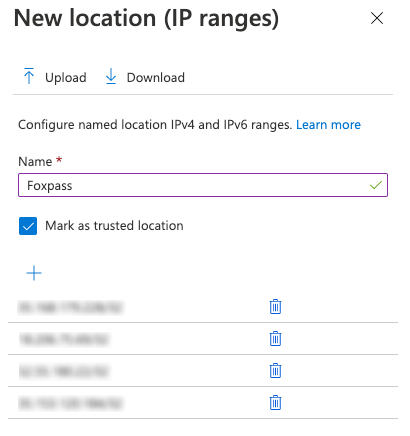
Foxpass named location
After you've created the named location, you will need to exclude Foxpass from MFA during sign-in requests. You can exclude all trusted locations, or just Foxpass specifically.
Go to Conditional Access Policy , select your policy, and then conditions --> Locations --> Configure -Yes, Exclude --> All trusted locations or just foxpass.
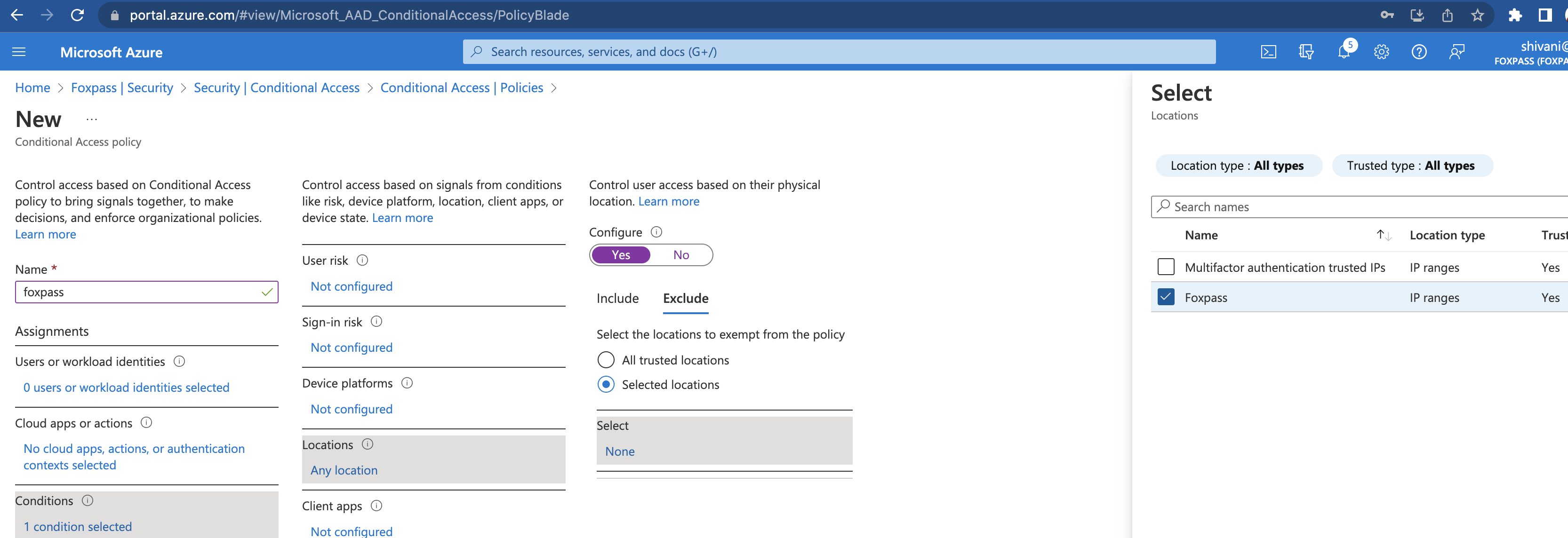
Exclude foxpass
Be sure to save any updated configurations. Afterwards, all delegated authentication requests from Foxpass should bypass MFA and Azure will allow the sign in request.
Debugging: Checking Azure's Access Logs
Sometimes, it's unclear why a login is failing. First, check your Foxpass LDAP or RADIUS logs. If users are failing with an error message like "Azure: LOGIN FAILED," then Azure is failing the login for an unspecified reason. You'll need to log into your Azure Active Directory admin center to check the logs to find the specific reason.
In the Azure Active Directory admin center, go to the Users section and select Activity -> Sign-ins. There you will see a list of attempted sign ins for your users.
Go to the User sign-ins (non-interactive) section and select a corresponding failed login from Foxpass. In the Basic Info section, the Failure Reason will explain why the login failed. The Conditional Access section will show which conditional access policies were applied.
Using these logs will help you debug the issue and unblock your users.
Troubleshooting
Error: AADSTS65001: The user or administrator has not consented to use the application
Solution: Authenticate to Foxpass using OAuth with an account that has permission to consent on behalf of the organization. Steps:
- Go to the login page .
- Click "Sign in with Microsoft"
- Sign in with an Azure Global admin.
- At the consent screen, check "Consent on behalf of your organization"
Error: AADSTS50076: Due to a configuration change made by your administrator, or because you moved to a new location, you must use multi-factor authentication to access.
Solution: Apply the conditional access policy that excludes MFA on Foxpass RADIUS IP addresses during authentication.
Updated 1 day ago
