Using Foxpass as a MFA Server for AWS Workspaces
Note: Foxpass MFA over RADIUS is part of our Advanced RADIUS add-on featureTo enable this feature, contact us at [email protected] or via the Intercom chat
Foxpass can be configured for use as an MFA server for AWS Workspaces. You can read more about the general setup process for enabling MFA in AWS Workspaces here:
https://aws.amazon.com/blogs/security/how-to-enable-multi-factor-authentication-for-amazon-workspaces-and-amazon-quicksight-by-using-microsoft-ad-and-on-premises-credentials/
After you've configured your Active Directory in AWS Workspaces, go to the RADIUS Servers page in Foxpass and create a new server. Then, set TOTP as Password to Yes. This will configure the RADIUS server to check MFA codes instead of passwords during authentication requests.
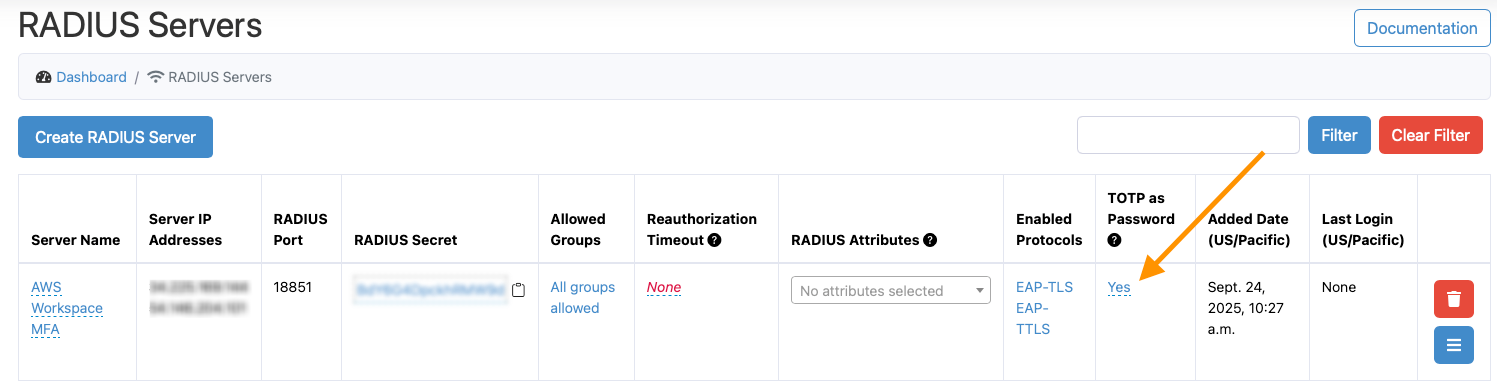
RADIUS Client configuration
Next, you'll need to add the Foxpass RADIUS details into the MFA section. In the AWS console, go to Directory Service > Active Directory > Directories. Select the Networking & security tab, and then in the Multi-factor authentication panel at the bottom of the page, select Actions > Edit.
Now, you'll need to enter in the Foxpass specific values for the MFA authentication.
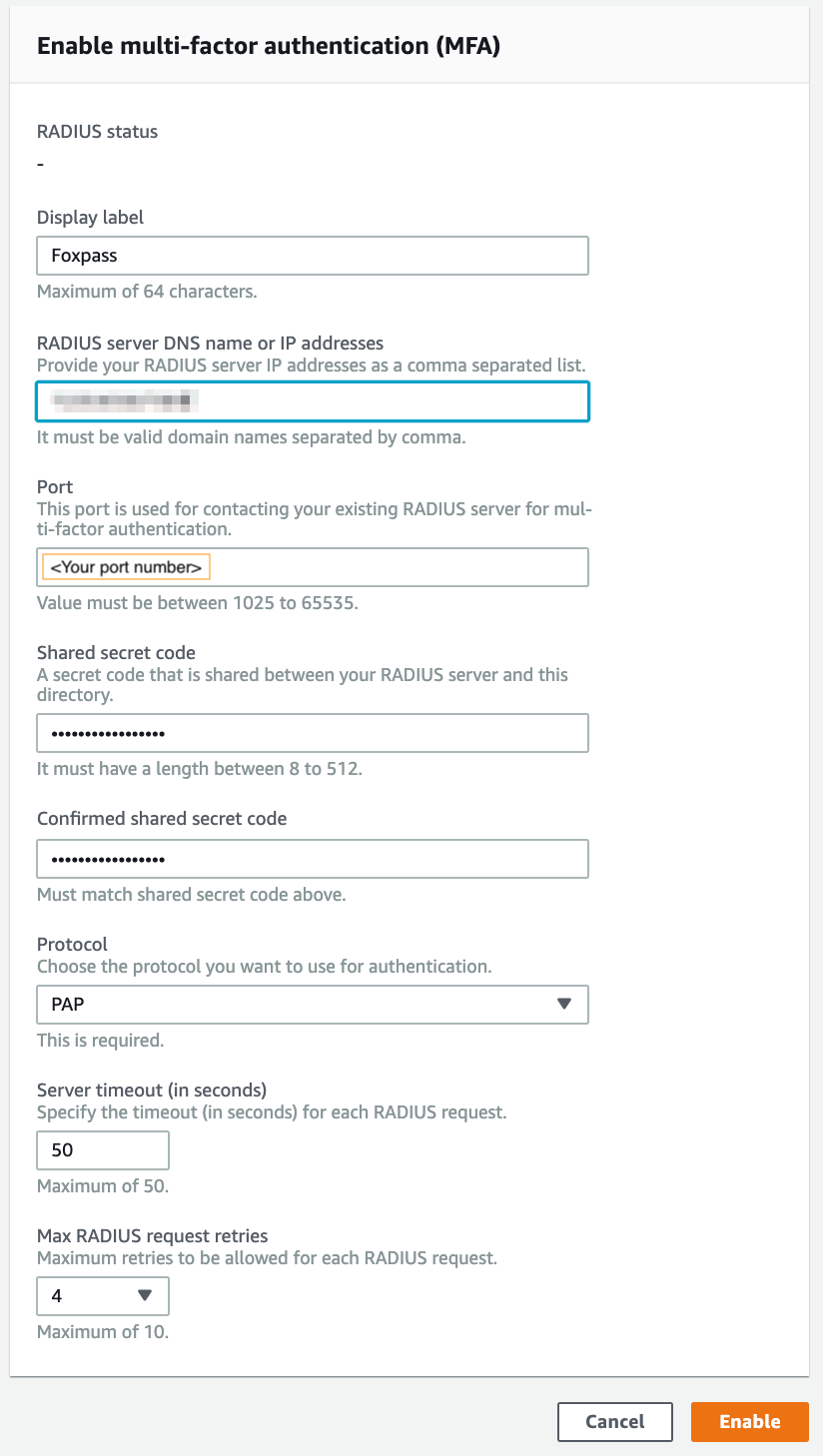
AWS Configuration
Display label: <Easily identifiable name>
RADIUS Server DNS Name or IP Address: <IP address - located on RADIUS Settings page > RADIUS Servers > Port Based RADIUS Server > IP addresses, as a comma-separated list
Port: <Your port number - located on RADIUS Settings page > RADIUS Servers > Port Based RADIUS Server > Port
Shared secret code: <RADIUS client secret from previous step>
Confirmed shared secret code: <same as above>
Protocol: PAP
Sever timeout: 50
Max RADIUS Request Retries: 4Finally, if you haven't yet, use an appropriate app to scan the QR code on the My Settings page in Foxpass to set up your TOTP MFA. Now, when logging into the Workspace, enter in the code from the app when prompted and you'll be good to go!
Foxpass QR code
Updated 3 months ago
