Intune-Windows
Configure EAP-TLS on Foxpass
Please follow the EAP-TLS initial setup guide to create client CA, server CA and SCEP endpoint if not configured already.
Configure Intune for Initial Setup
If you are configuring SCEP certificates for both Windows and macOS, you only need to follow the initial setup documentation once
Please refer the Intune for Initial Setup documentation to configure Intune initially.
Create Configuration profiles
In the Endpoint manager, now go to devices → configuration profiles
Four(4) Configuration profiles will be generated for Client CA, Server CA, SCEP Certificate, and WiFi Profile.
- Create a new profile for Windows 10 using the Trusted certificate template. Upload the Foxpass Client CA in the client profile.
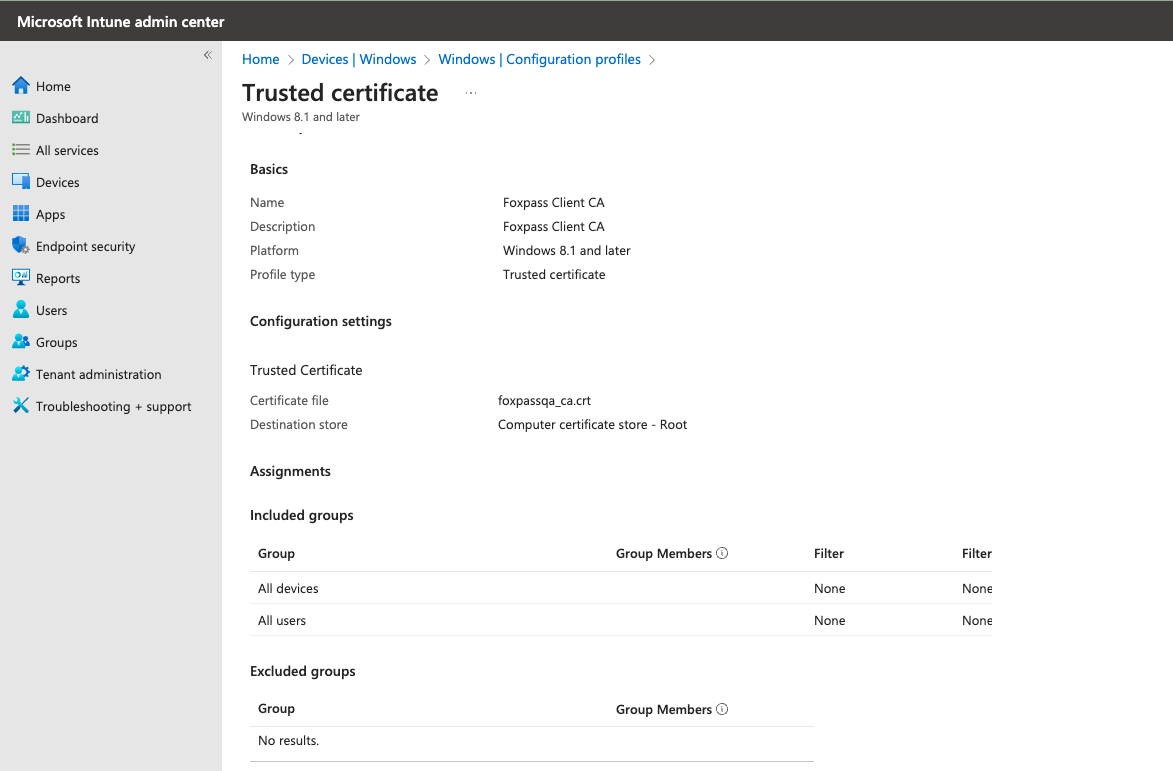
Foxpass Client CA profile
- Create a new profile for Windows 10 using the Trusted certificate template. Upload the Foxpass Server CA cert in the server profile.
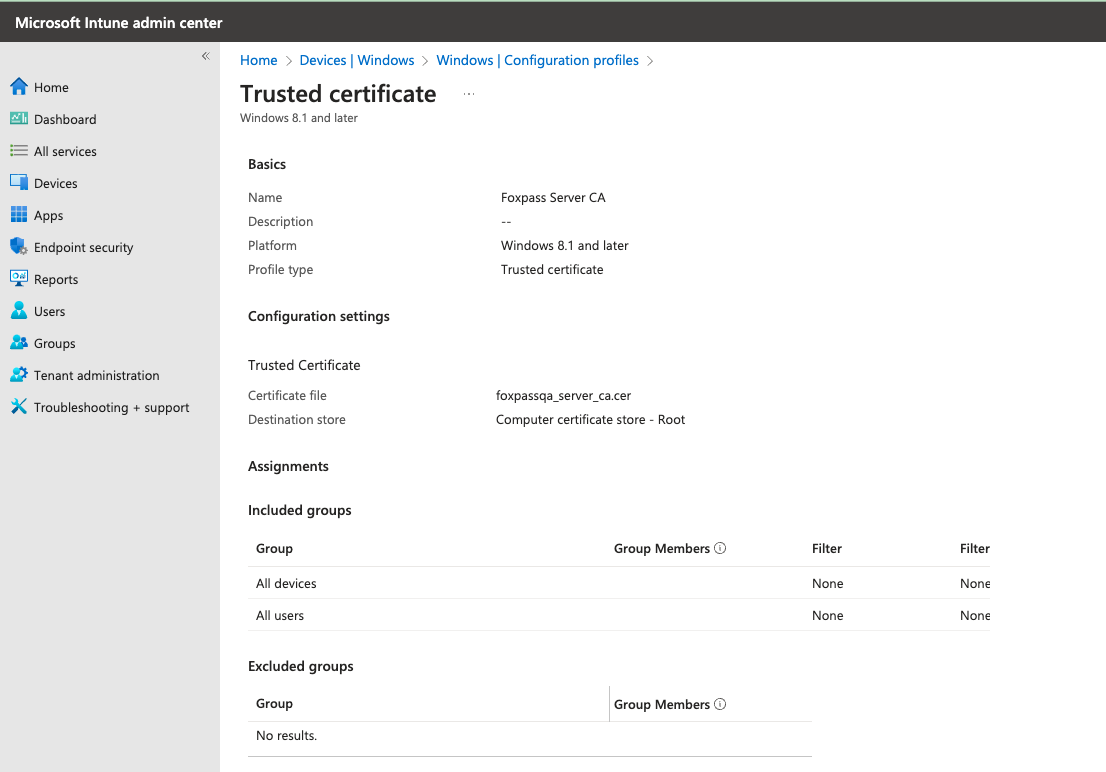
Foxpass Server CA Profile
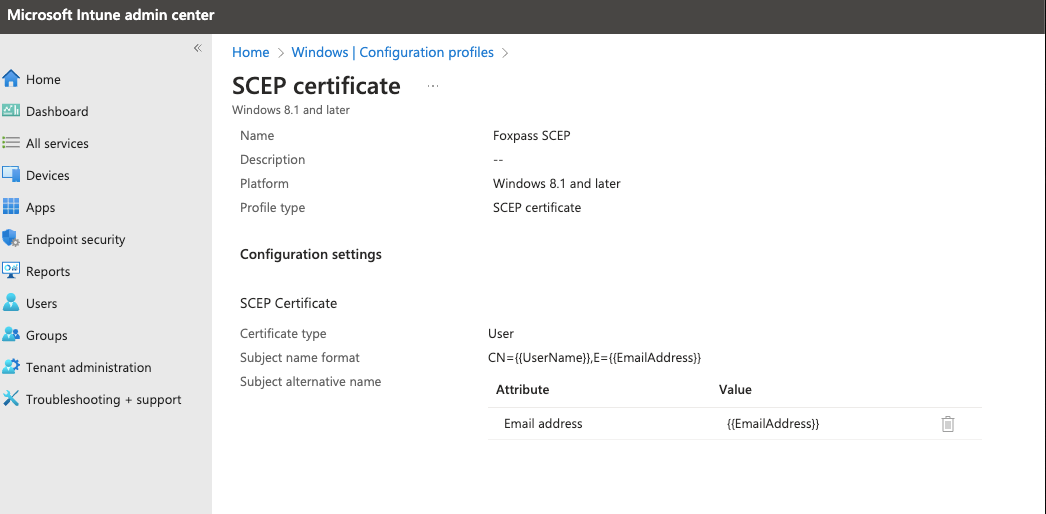
- Create another new profile for Windows 10 using the SCEP certificate template . You can create a profile with either the "User" or "Device" certificate type, depending on your specific use case and requirements.
Option 1: Certificate type - User
For certificate type user, verify if the SCEP settings have been correctly configured in Foxpass.
You need to make sure that every user has an EmailAddress set in their Azure User Profile. If not, SCEP the profiles will not install.
- Name: Foxpass SCEP
- Certificate type: User
- Subject name format: CN={{UserName}},E={{EmailAddress}}
- Subject alternative name: Add attribute:
- Email address as {{EmailAddress}}
- URI as IntuneDeviceId://{{AAD_Device_ID}} (This is required if you want to check device compliance during EAP-TLS request)
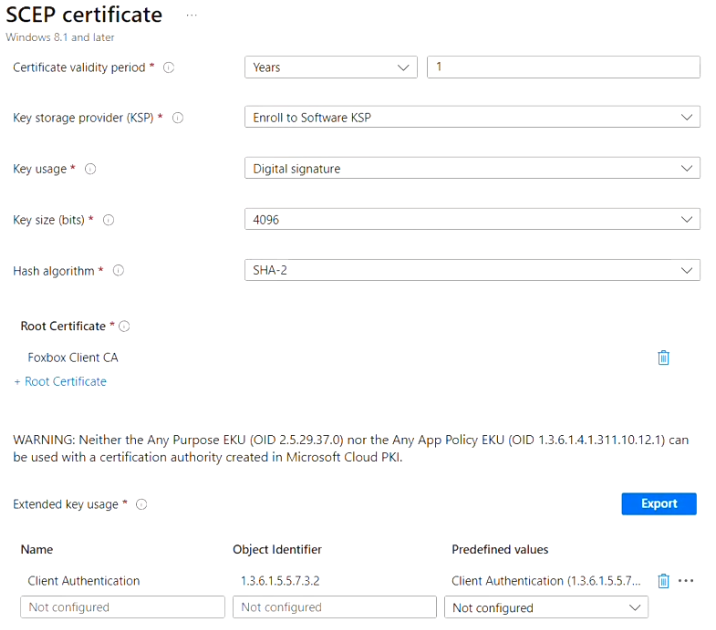
- Certificate Validity period: Years = 1
- Key storage provider: Enroll to software KSP
- Key usage: Digital Signature
- Key size: 4096
- Hash algorithm: SHA2
- Root certificate: Select cert from Foxpass Client CA from first item in this section
- Extended key usage:
- Add Client Authentication (1.3.6.1.5.5.7.3.2)*
- Renewal threshold (%): 10
- SCEP server URL: Foxpass SCEP endpoint from the SCEP page
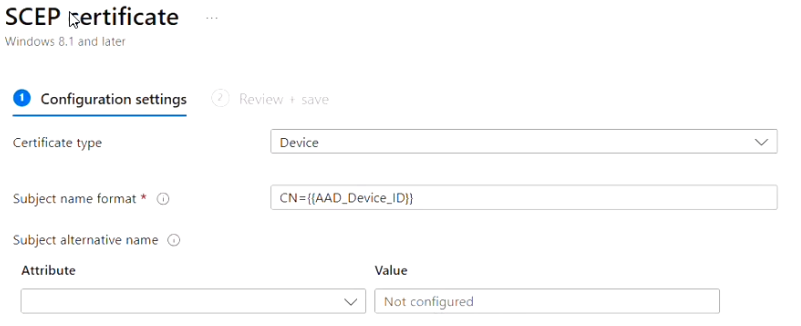
Option 2: Certificate type - Device
For certificate type device, verify if the SCEP settings have been correctly configured in Foxpass.
To configure the Device certificate type, you have two options: either Sync devices from Azure on the Devices page, or select 'None' for the verification type when creating an SCEP endpoint on the SCEP page.
- Name: Foxpass SCEP
- Certificate type: Device
- CN={{AAD_Device_ID}}
- Subject Alternative Name: Leave it empty.
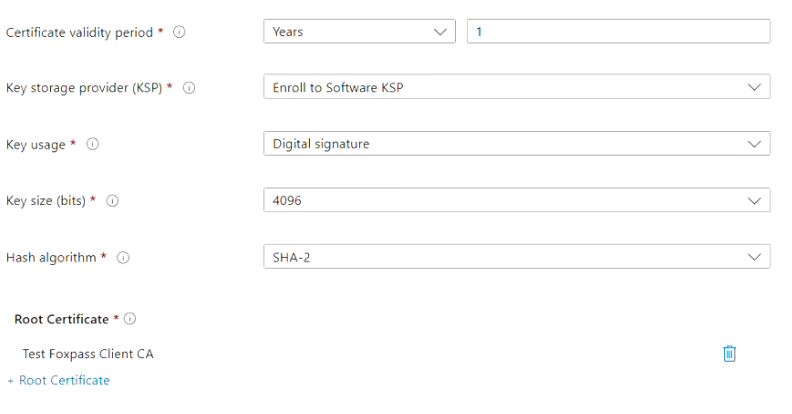
- Certificate Validity period: Years = 1
- Key storage provider: Enroll to software KSP
- Key usage: Digital Signature
- Key size: 4096
- Hash algorithm: SHA2
- Root certificate: Select cert from Foxpass Client CA from first item in this section
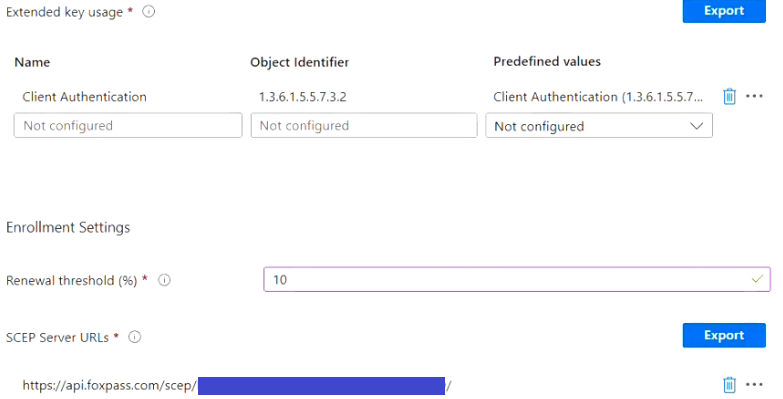
- Extended key usage:
- Add Client Authentication (1.3.6.1.5.5.7.3.2)*
- Renewal threshold (%): 10
- SCEP server URL: Foxpass SCEP endpoint from the SCEP page
-
Create a new Wi-Fi profile with these settings:
Advanced settings (Required)
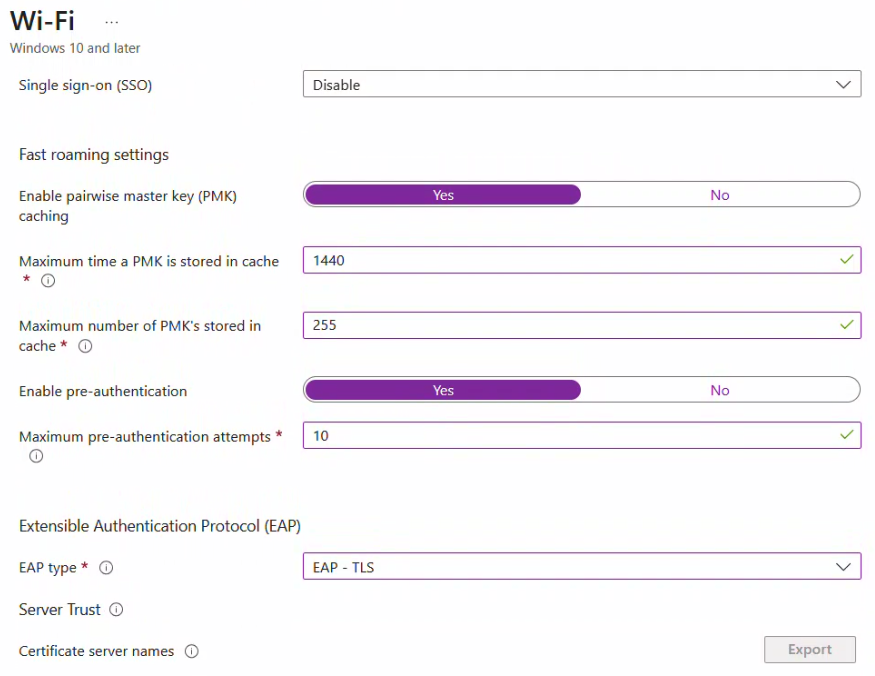
Important for Windows 10/11 EAP-TLS stability: When Windows 10/11 devices have multiple client certificates installed (for example, a domain-issued machine certificate alongside a Foxpass SCEP certificate), roaming without fast roaming enabled and properly configured can cause Windows to re-run certificate selection and present an unintended certificate during authentication. Configure the following settings to prevent this behavior:- Enable fast roaming: Yes
- Enable pairwise master key (PMK) caching: Yes
These settings prevent full EAP renegotiation during roaming and ensure Windows continues using the originally selected Foxpass certificate.
- Wi-Fi name: Foxpass
- Connection name: (Your SSID)
- Connect automatically: (your choice)
- Hidden network: Disable
- Authentication Mode: Select User for a user certificate and Machine for a device certificate.
- Proxy settings: None
- EAP-Type: EAP-TLS
- Root certificates for server validation: (Choose Foxpass Server CA uploaded previously in this step)
- Certificates: Foxpass SCEP
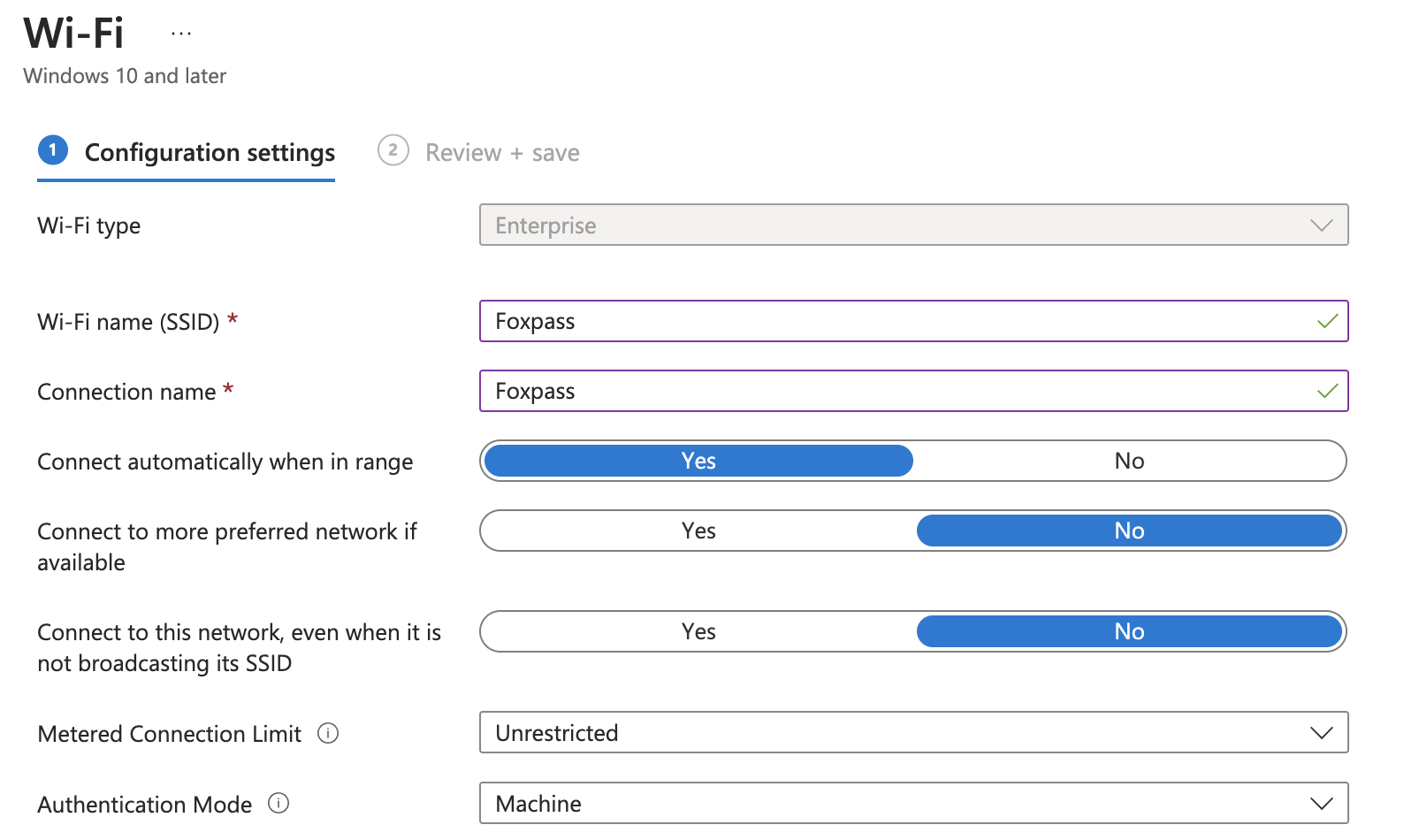
Wi-Fi Settings for a device certificate
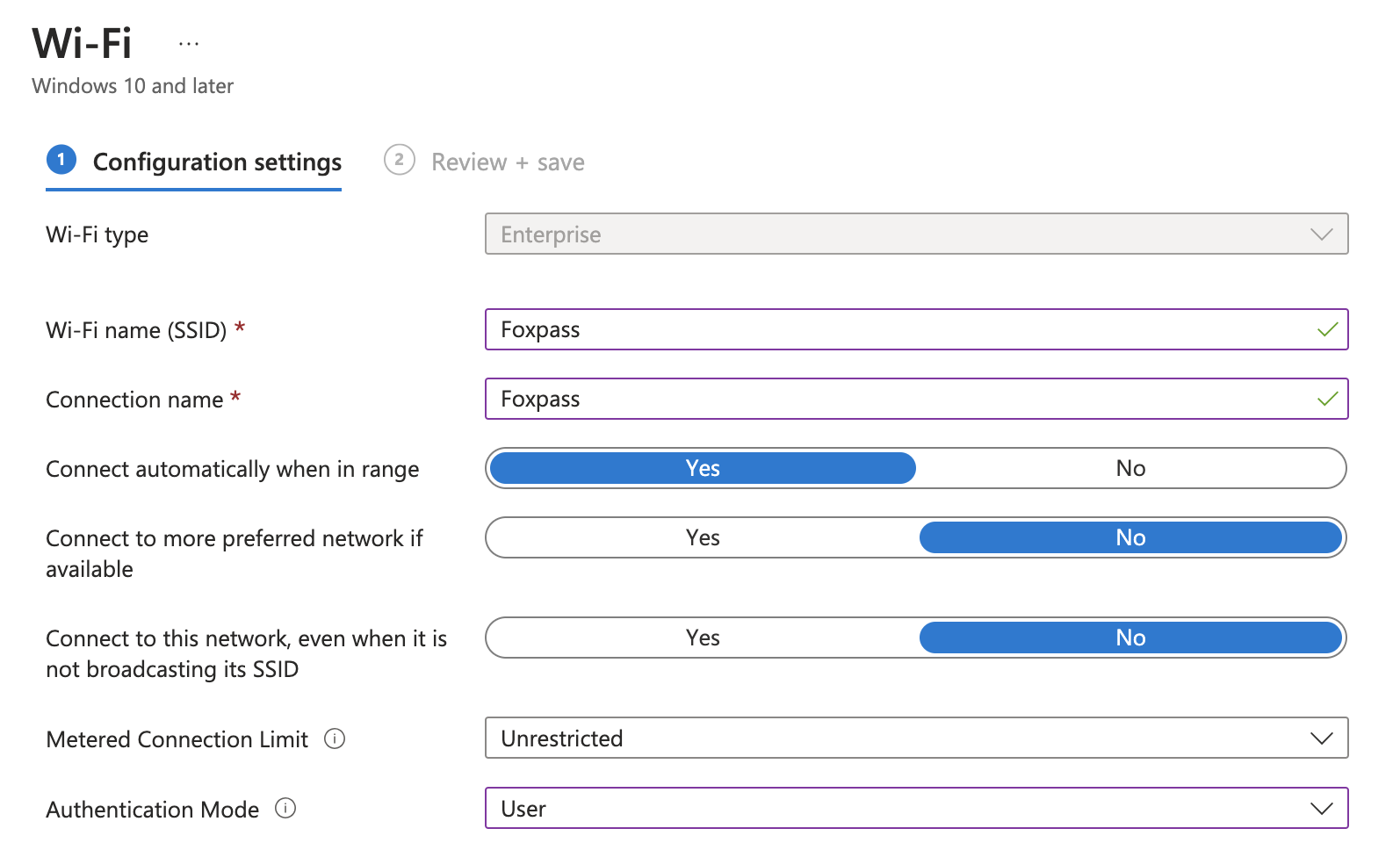
Wi-Fi Settings for a user certificate
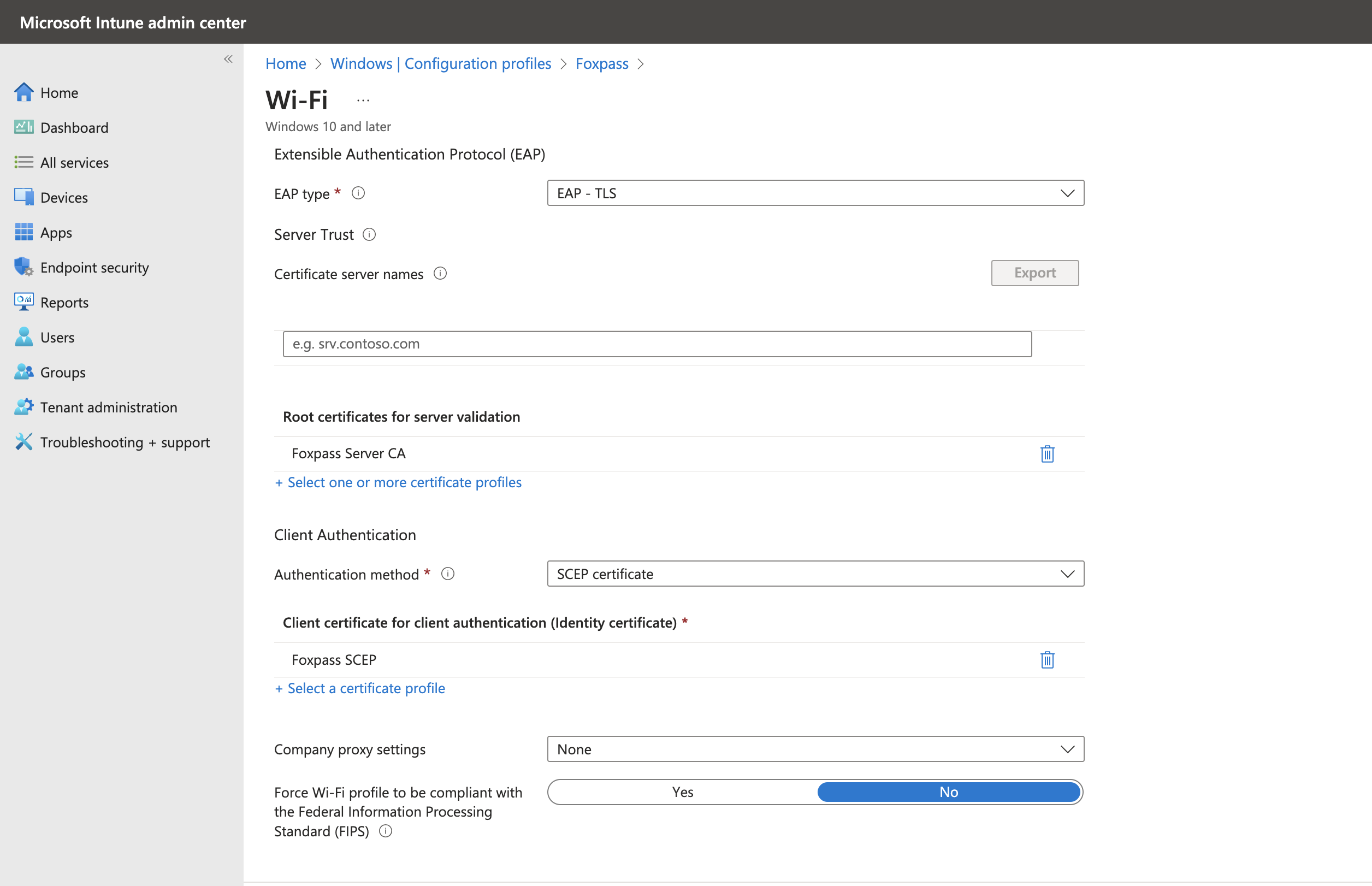
Now, test
Test by enrolling a sample Windows 10 device: Open settings → Access work or school → Enroll device MDM → Enter your company email and proceed to login to Azure. This will kick off the enrollment process that takes a little while.
If all goes well, you will now be able to see your device enrolled in Intune and the Foxpass Console's EAP-TLS.
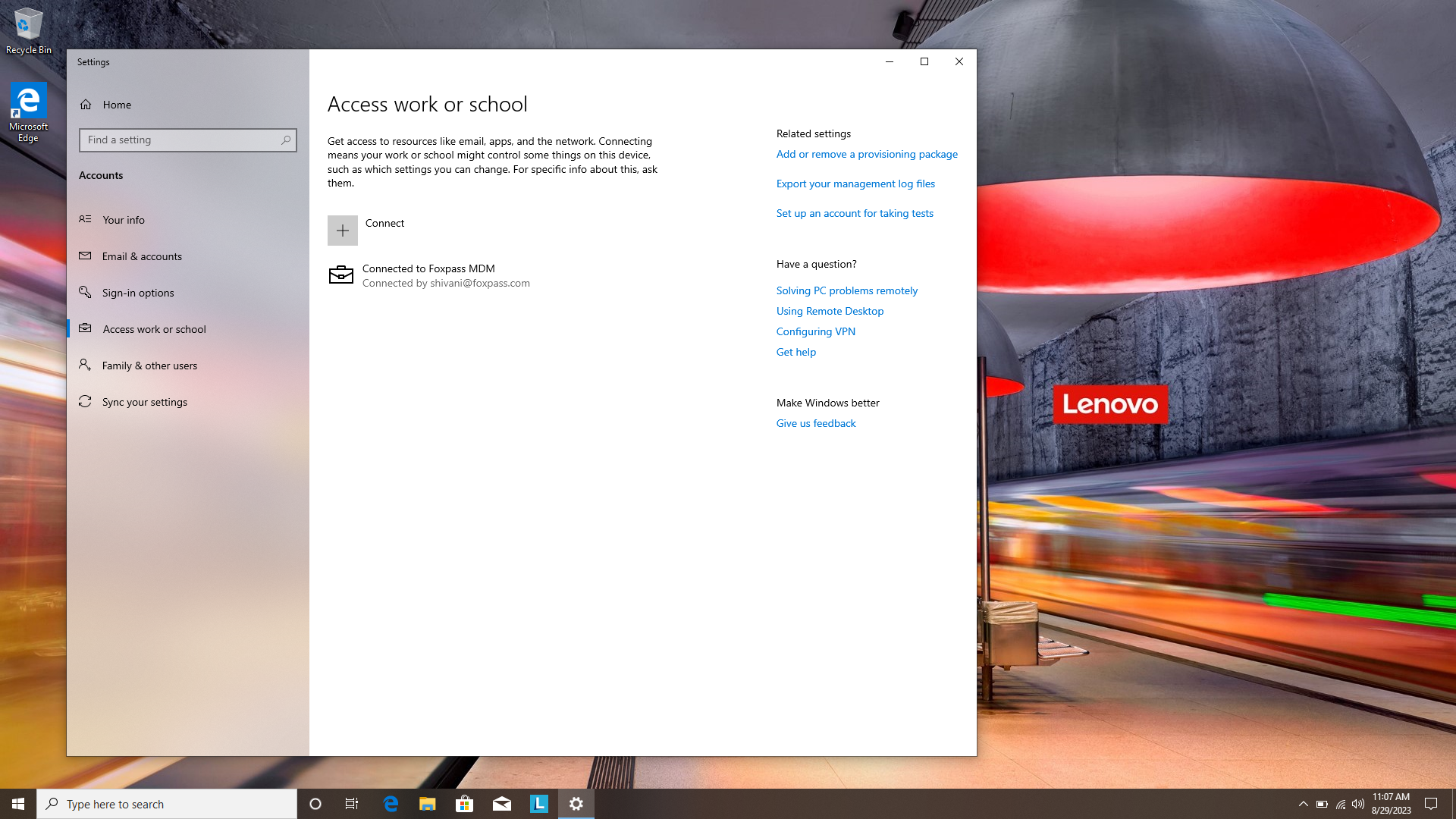
Windows connected to Foxpass MDM
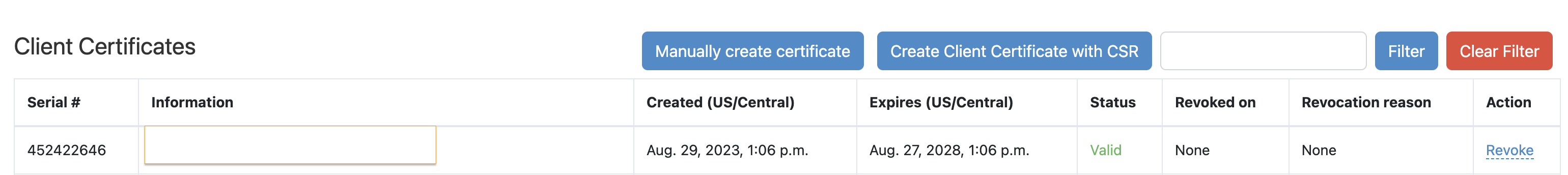
Client Certificate - Intune
You can see Foxpass Client CA and Server CA in "Certificates" under "Trusted Root Certificate Authorities" on your Windows machine.
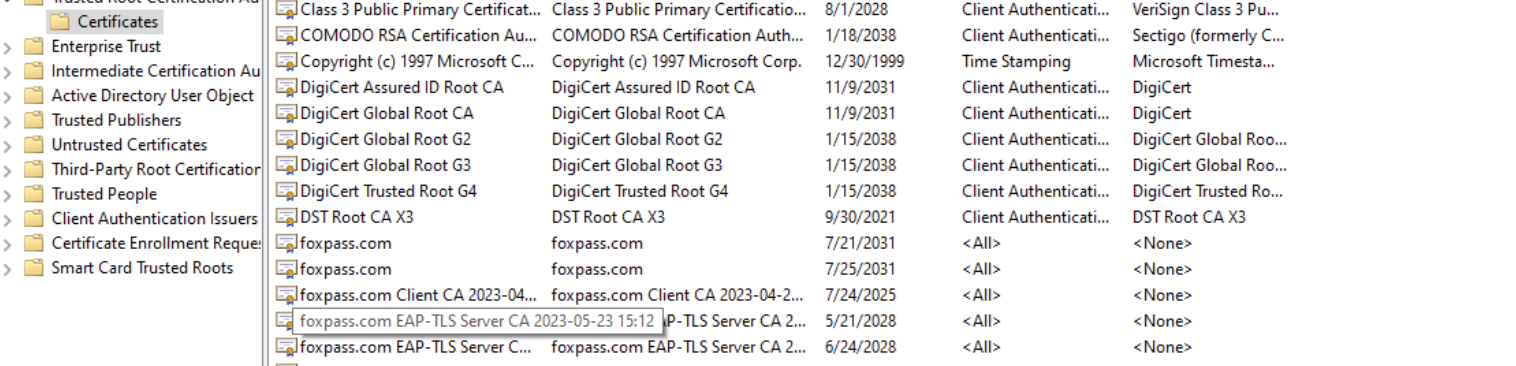
Client CA and Server CA in Windows
You can view your Client certificate in "Certificates" under "Personal" category.
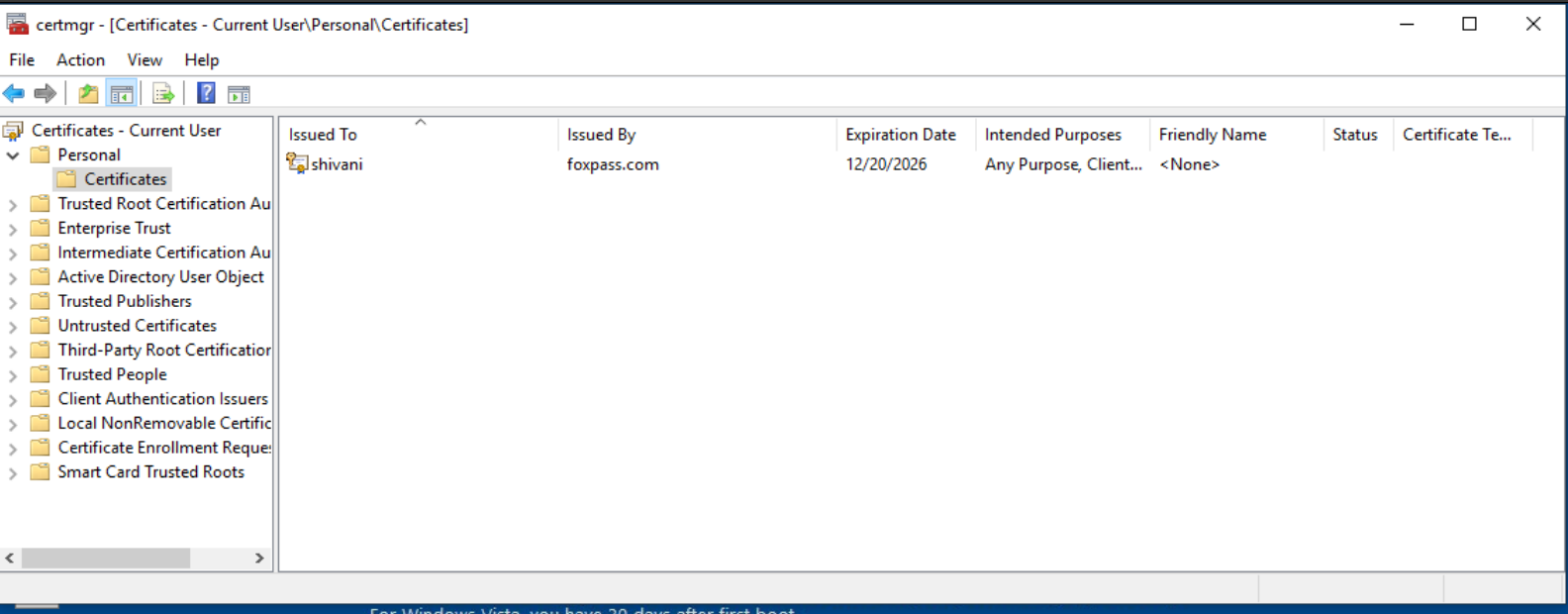
Client certificate
You can also see successful/unsuccessful logs on the RADIUS logs page.
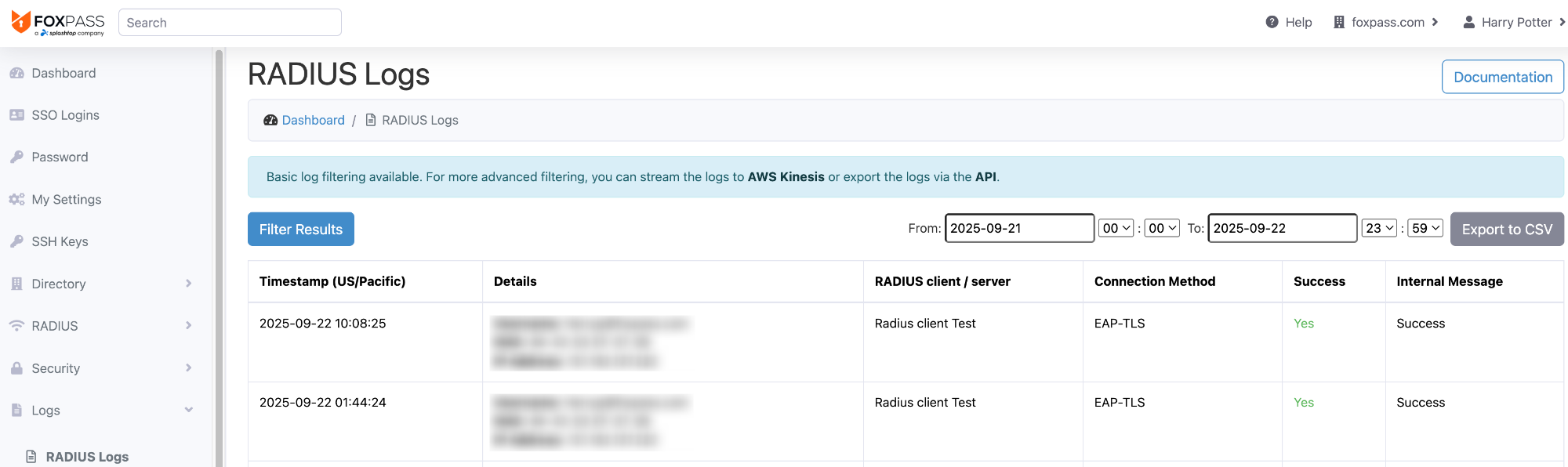
RADIUS logs page
Still having problems?
Updated 3 months ago
